Tech Council
Technology Articles
Cloud Modernization Strategy Guide for Enterprises 2026
Avoid costly mistakes in cloud modernization. Learn planning best practices, how strategy optimizes budget, and practical steps to reduce risks.

Denis Avramenko
CTO, Co-Founder, Streamlogic
Dec 18, 2025

Reading time: 20 min
Before starting cloud modernization: assess your infrastructure, choose the right approach for each application, then build a phased roadmap with realistic budgets. Projects that skip this sequence hit budget overruns and extended timelines.
IDC's Cloud Pulse Survey (Q3 2024) found 82% of surveyed companies need cloud modernization, with 60% requiring major IT infrastructure transformation. The same research shows 88% use hybrid cloud and 79% multi-cloud environments for vendor flexibility and data sovereignty.
This guide covers infrastructure assessment, application-specific approaches, implementation sequencing, budget planning, and compliance frameworks.
Table of Contents
What cloud modernization means for your business
Migration vs modernization: making the right choice
What happens when you start without a strategy
Common mistakes when planning modernization
How to assess your current infrastructure
Choosing the right approach for each application
Building a phased roadmap that minimizes risk
Budget planning and cost control
Security and compliance considerations
What cloud modernization means for your business
Cloud modernization transforms legacy applications and infrastructure to run on modern cloud platforms. Migration moves existing systems to cloud infrastructure without architectural changes — the application runs on cloud servers instead of on-premises hardware, but the code and architecture stay the same. Modernization rebuilds applications to leverage cloud-native capabilities: automated scaling, managed databases, container orchestration, and distributed architectures.
Companies modernize to enable faster deployments and reduce operational overhead. System resilience improves when failures in one component don't cascade across the entire application. Monolithic applications get rearchitected into smaller components. Teams adopt container orchestration. Infrastructure automation replaces manual processes. These changes allow independent deployments rather than coordinated releases across entire systems.
Modernization introduces complexity. Distributed architectures need sophisticated monitoring across multiple components. Teams need expertise in container platforms and distributed system patterns. Network configuration becomes more involved. Moving from monolithic applications to microservices often reveals underestimated operational overhead when managing dozens or hundreds of services.
Hybrid and multi-cloud deployments have become the dominant model. Companies combine on-premises infrastructure with public cloud services to meet data sovereignty requirements and avoid vendor dependency. Cost optimization plays a role in platform selection. Some workloads remain on-premises due to regulatory constraints or latency requirements.
Table 1: What Changes During Modernization
Aspect | Before Modernization | After Modernization |
Deployment frequency | Weekly or monthly releases | Daily deployments possible |
Scaling | Manual capacity planning | Automated scaling for variable loads |
Infrastructure costs | Fixed capacity expenses | Usage-based pricing (with reserved capacity options for predictable workloads) |
Failure isolation | Single failure can affect entire system | Component failures contained to specific services |
Operational complexity | Centralized management | Distributed systems with multiple monitoring points |
Migration vs modernization: making the right choice
Cloud migration moves applications to cloud infrastructure without changing their architecture. Cloud modernization rebuilds the applications themselves to use cloud-native patterns and services.

Migration moves existing systems to new infrastructure. A financial processing system running on on-premises servers moves to cloud virtual machines. The application code, database schema, and integration points remain unchanged. Setup takes weeks because teams work with familiar architecture.
Modernization redesigns the application. The same financial system gets rebuilt with managed database services, event-driven processing, and automated scaling based on transaction volume. Teams can update the payment module without touching the reporting system.
When migration fits
Data center contracts expire within months
Budget covers infrastructure moves but not development work
Applications face retirement within two years
Teams lack cloud-native development expertise
Many companies migrate first to establish cloud operations expertise, then modernize applications based on business priority.
When modernization delivers value
Applications expected to run five years or longer
Current architecture can't handle doubled traffic
Business needs weekly releases instead of quarterly
Operational costs justify upfront investment
Modernization costs more upfront and requires more technical expertise. Applications built for cloud platforms often show lower operational costs over time.
Table 2: Migration vs Modernization
Factor | Migration | Modernization |
Code changes | Minimal configuration adjustments | Significant architectural redesign |
Timeline | Weeks to months depending on complexity | Months to over a year for complete transformation |
Cost structure | Lower initial investment | Higher upfront costs, potential long-term savings |
Risk level | Lower technical risk, familiar patterns | Higher risk, requires cloud-native expertise |
Reversibility | Straightforward to move back | Complex but possible with proper abstraction |
Best for | Short-term moves, budget constraints | Strategic applications, long-term operations |
Beyond these two options, approaches exist that combine migration with selective optimization. Hybrid architectures keep portions on-premises while moving others to cloud.
What happens when you start without a strategy
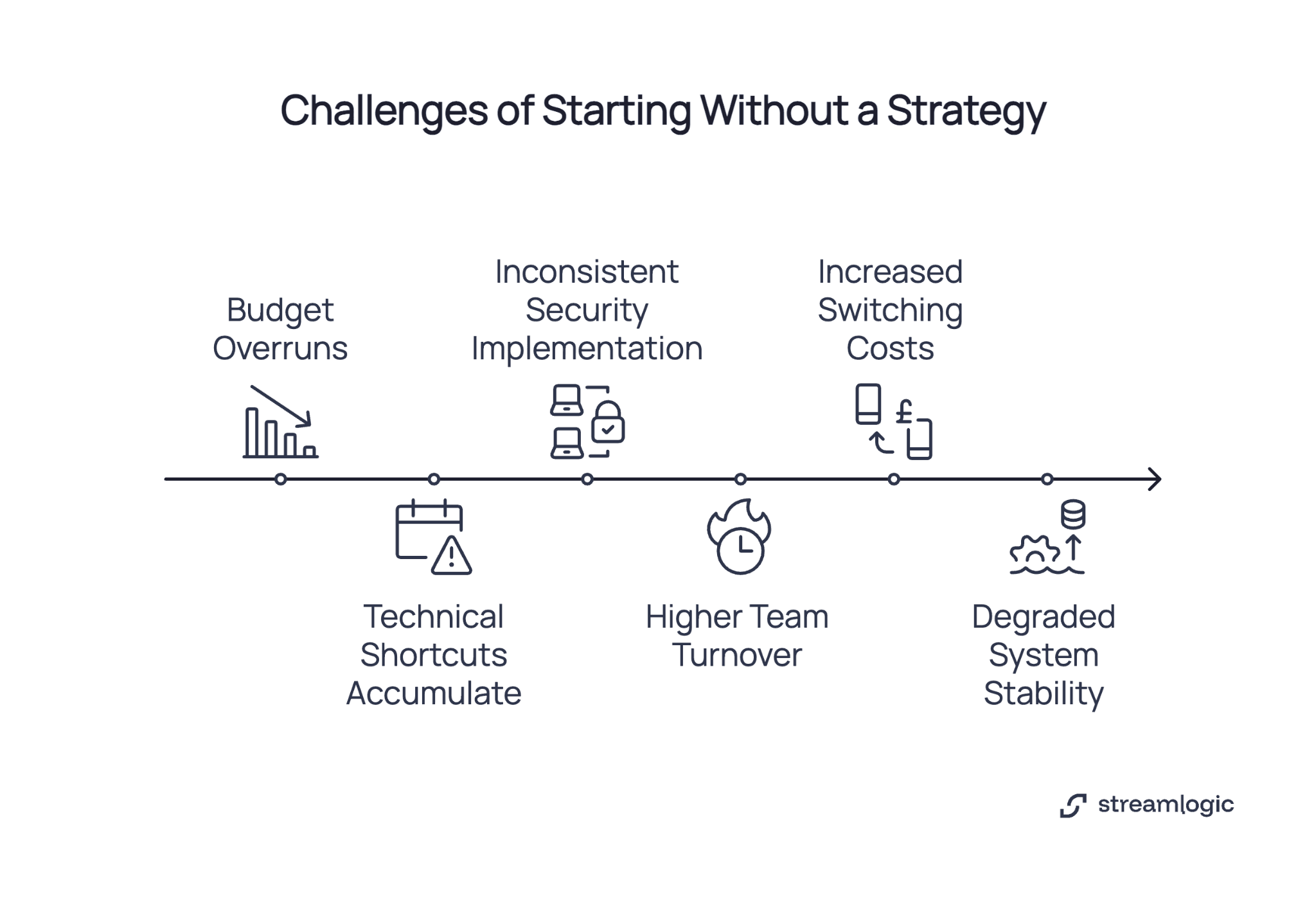
Projects without planning tend to hit the same problems. Industry data shows recognizable patterns when organizations skip strategy development.
Common challenges:
Budget overruns. Initial estimates often prove incorrect. Teams discover unexpected dependencies during execution. What seemed like a three-month project can extend to six or nine months, with corresponding cost increases.
Technical shortcuts accumulate. Deadline pressure leads to quick fixes that weren't meant to be permanent. Some get addressed later. Many don't. Each unresolved shortcut makes future changes harder.
Inconsistent security implementation. Without coordination, different teams apply different security standards. Some applications receive thorough hardening. Others get basic protection. The gaps usually surface during audits or when something breaks.
Higher team turnover. Extended timelines and constant firefighting affect morale. Some experienced engineers move to other opportunities. Knowledge transfer becomes a challenge when this happens.
Increased switching costs. Teams often choose services based on immediate fit rather than long-term flexibility. Over time, these choices can make changing providers expensive and complex.
Degraded system stability. As projects drag on without clear direction, maintenance windows grow longer. Performance issues become more frequent. User experience suffers, which stakeholders notice.
Fixing these issues mid-project costs more than preventing them. Projects often require pausing ongoing work, assessing what's accumulated, and adjusting course. A cloud modernization strategy helps by establishing priorities, realistic budgets, and coordination frameworks before work starts. Not every project without strategy fails, but the pattern appears often enough to merit attention.
Common mistakes when planning modernization
Mistake 1: Updating everything at once
The pressure for fast results pushes all applications into simultaneous modernization. Dependencies show up fast: Team A waits on Team B to finish database schema changes, Team C can't deploy until Team A completes. Nothing ships for months. Start with 2-3 applications and apply those learnings to the next batch.
Mistake 2: Assuming your current team has the skills
The assumption: existing team will figure out cloud-native architecture on the job. Reality: unfamiliar technologies slow everything down by 2-3x. What looked like cost savings from skipping training becomes project delays that cost far more. Plan 3-6 months for training or budget for external expertise before starting.
Mistake 3: Picking technology before understanding requirements
Without cloud skills, teams don't know how to evaluate requirements. So they choose what successful companies use - microservices, serverless, Kubernetes. Then discover the operational complexity doesn't fit a 4-person team. Managed Kubernetes services reduce some operational overhead, but still require expertise in container orchestration, networking, and distributed system patterns. Pick technology based on actual requirements and team capacity.
Mistake 4: Underestimating data migration
Data migration gets underestimated because it looks like a simple copy operation on paper. In practice, schemas need translation, data quality issues surface, and volume estimates prove optimistic. Migration tools like AWS Database Migration Service or Azure Data Migration Service handle technical transfer, but don't solve schema incompatibilities or data quality problems. Test data migration at production scale before the actual cutover, because discovering problems during go-live is expensive.
Mistake 5: Skipping success metrics
Success metrics get skipped in the rush to start. Nobody wants to slow down project kickoff with measurement discussions. Six months later, Engineering says performance improved while Finance says costs increased. Both are right because nobody defined what success meant upfront. Establish metrics before starting - deployment frequency, response times, costs - and track them monthly.
Mistake 6: Adding security and governance late
Security involvement gets delayed because architecture discussions feel like purely an engineering problem. When security finally reviews locked-in decisions, compliance violations require re-architecting core services. Months of delay, hundreds of thousands in rework. Involve security during initial architecture discussions when changes are still cheap.
Mistake 7: Skipping proper test environments
Production-equivalent environments have ongoing costs, so they get cut to save budget. Then production launch reveals what happens under real load: performance degrades, systems crash, customers can't access services. Emergency fixes cost 10x the monthly environment cost. Test at scale before launch, or pay significantly more fixing issues under customer pressure.
A cloud modernization strategy addresses these mistakes during planning when prevention costs less than recovery.
Table 2: Common Mistakes and Their Prevention
Mistake | Why It Happens | Real Consequence | Prevention |
Simultaneous modernization | Pressure for fast results | Teams blocked waiting on each other, nothing ships for months | Start with 2-3 apps, learn, then scale |
Skipped capability assessment | Assumption team will learn on the job | Tasks take 2-3x longer, project delays compound | 3-6 month training plan or external expertise |
Technology-first selection | No cloud skills to evaluate needs | Operational complexity team can't manage | Match technology to actual requirements and team size |
Data migration assumptions | Looks simple on paper | Schema issues, data quality failures at cutover | Test at production scale before go-live |
No success metrics | Rush to start without measurement discussions | Engineering vs Finance arguments with no data | Define and track metrics from day one |
Late security integration | Architecture feels like purely engineering problem | Re-architecture costs, months of delay | Security involved in initial architecture discussions |
Insufficient testing | Monthly environment costs seem expensive | Production failures, emergency fixes cost 10x more | Production-equivalent test environments |
How to assess your current infrastructure
Assessment tells you what you have before deciding what to change. Dependencies between applications get overlooked. External partner integrations get missed. Knowledge concentration risks stay invisible until someone leaves. Discovering these mid-project costs significantly more to fix.
Week 1: Critical minimum
Start with an application list. What runs the business, who owns it. Spreadsheet detail works here. Teams of 2-3 people working part-time can typically complete this for environments with 20-50 applications. Larger estates need more time or dedicated resources.
Data dependencies affect sequencing. App B pulls data from App A. Modernizing B requires A compatibility, though adapter layers provide temporary solutions. Map these flows now, or teams wait on blocked dependencies. Application performance monitoring tools automate dependency mapping, but manual validation catches what automation misses.
External integrations create business risk. Partner API integrations, vendor file transfers, third-party database connections - document these before changes begin. Breaking a partner's API during migration degrades their ability to send orders or process payments.
Knowledge concentration stays invisible until someone leaves or gets reassigned. Systems that only one person understands create operational risk. Flag these systems and plan knowledge transfer.
Compliance constraints come next. Healthcare data needs HIPAA. Payment processing needs PCI-DSS. These determine cloud provider selection. AWS supports FedRAMP for government workloads. Azure offers government cloud regions with specific compliance certifications. GCP provides assured workloads for regulated industries.
One week typically covers this minimum for smaller environments. Output enables application prioritization and identifies major blockers.
Weeks 2-4: Full picture
Extended assessment adds depth and requires dedicated resources or external help. Document current performance - response times, throughput, error rates. Without baselines, proving improvement becomes difficult.
Technical debt varies across applications. Some systems have solid code quality. Others have zero test coverage and documentation one person wrote years ago. Catalog what exists.
Infrastructure assets have financial implications. Servers, storage, networking equipment, licenses carry costs and depreciation schedules. For hybrid architectures, this inventory determines which workloads stay on-premises and which move to cloud based on regulatory requirements, latency needs, or cost optimization.
Full assessment takes 2-4 weeks with dedicated resources for organizations with 50-200 applications. Output is a structured report with application categories, dependency maps, cost analysis, and risk assessment.
What to do with results
Some applications work fine with minimal changes. Others need modernization to meet business goals. Some cost more to modernize than the benefit justifies.
Red flags need attention:
Critical (address before starting):
Compliance violations in current setup
Single points of failure that could stop revenue
Important (plan during assessment):
End-of-life software without replacement plans
Undocumented critical systems requiring knowledge transfer
Address critical red flags before starting modernization. If timeline pressure prevents completing full assessment, at minimum identify dependencies and compliance constraints before committing to delivery dates.
Choosing the right approach for each application
Choosing the right approach for each application
Three primary approaches handle most modernization scenarios. The decision depends on application characteristics, business requirements, team capability, and expected operational lifespan.
Replatforming: Minimal change, quick execution
Move applications to cloud infrastructure with minor configuration adjustments. Code and architecture remain largely unchanged. Works for applications on expensive infrastructure or systems with shorter lifespans. Implementation takes weeks to months. Struggles when performance improvements or architectural changes are needed.
Refactoring: Code optimization for cloud
Modify code to use cloud-native services while keeping overall architecture. Self-managed databases get replaced with managed services. Caching improves response times. Automated scaling handles variable loads. Implementation extends to months. Suits core applications with multi-year operational plans. Fails when fundamental architecture issues exist.
Rearchitecting: Complete transformation
Rebuild using cloud-native patterns where monoliths become microservices. Implementation measures in quarters. Targets strategic applications with 5+ year lifespans. Proves excessive for simple applications.
Example: Logistics tracking system
Replatforming moves servers and databases to cloud instances without code changes. Refactoring replaces the self-managed database with managed cloud services, implements caching for routes, and adds automated scaling. Rearchitecting breaks the monolith into independent services. Teams can update delivery notifications without touching route planning.
Table 3: Approach Selection Framework
Approach | Code Changes | Implementation Time | Works well for |
Replatforming | Minimal configuration | Weeks to months depending on complexity | Quick cloud presence, reduced infrastructure costs |
Refactoring | Moderate modifications | Months | Performance optimization, managed service adoption |
Rearchitecting | Complete redesign | Quarters to year+ | Strategic applications, fundamental capability changes |
The 7Rs framework (Rehost, Relocate, Replatform, Refactor, Repurchase, Retire, Retain) describes additional strategies. Retire eliminates applications no longer needed. Retain keeps workloads on-premises when regulatory requirements make cloud migration impractical.
Building a phased roadmap that minimizes risk
Phased implementation reduces risk by limiting what changes at once. Each phase builds capability needed for the next.
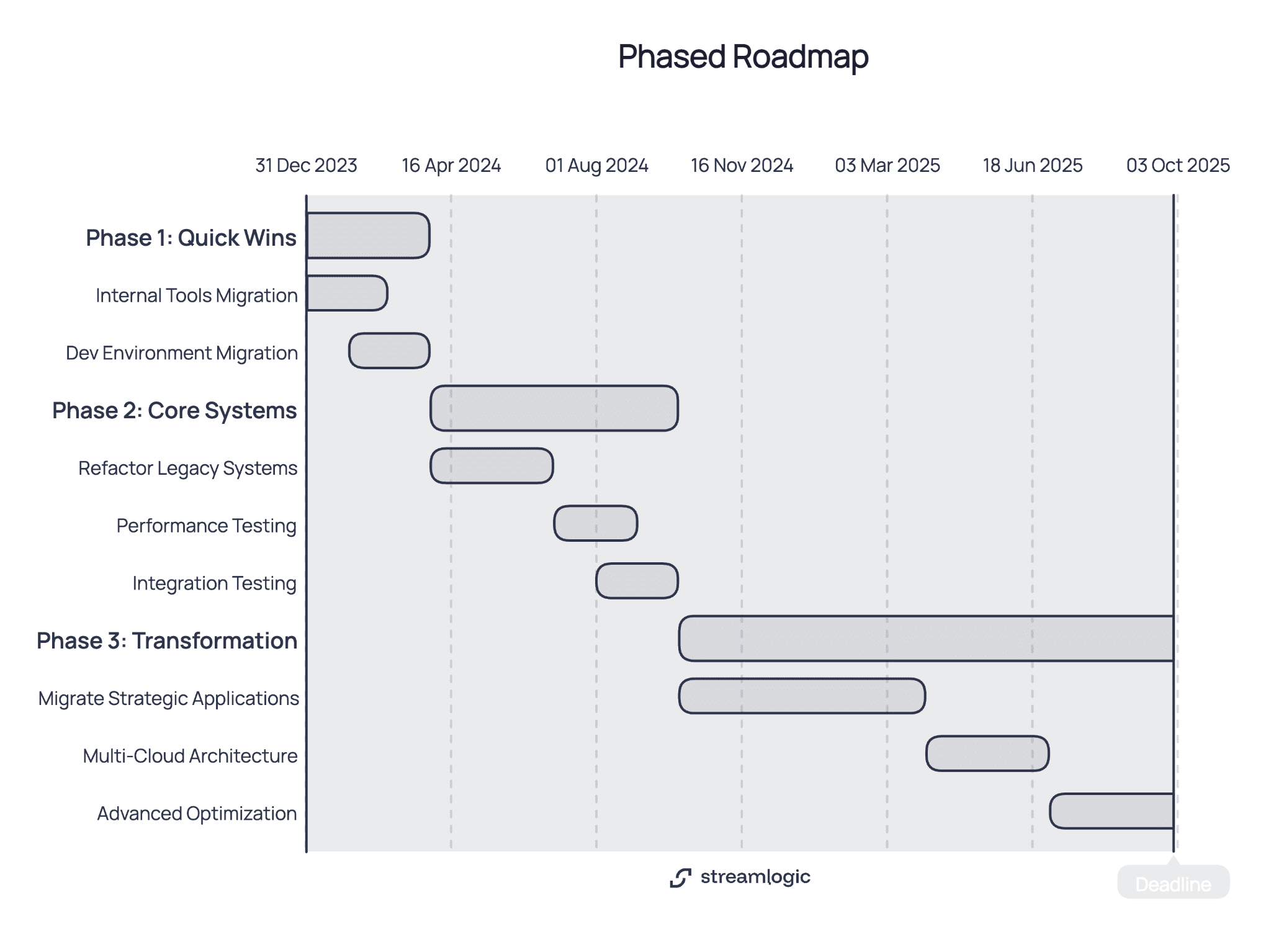
Phase 1: Quick wins (1-3 months)
Typically begin with 2-3 low-risk applications. Internal tools, development environments, or non-customer-facing applications work well. Teams gain initial cloud platform experience. The cloud migration strategy gets tested in practice. Stakeholders see progress. Document what works and what doesn't before moving forward.
Dependencies can extend Phase 1 timelines. An internal reporting tool that pulls data from customer-facing systems needs those integration points documented first. If Phase 1 reveals fundamental capability gaps or technical blockers, address these before touching business-critical systems. Advance to Phase 2 when teams demonstrate consistent execution and the approach proves viable.
Phase 2: Core systems (3-6 months)
Business-critical applications that need refactoring or rearchitecting legacy systems become the focus. Complexity increases, requiring more planning and testing. Performance testing happens at scale. Integration testing covers dependent systems.
Teams need established DevOps practices before Phase 2. Automated deployments reduce manual errors. Monitoring catches issues early. Incident response procedures ensure quick resolution. Without these foundations, risk increases significantly.
Phase 3: Complete transformation (6-12+ months)
This phase covers remaining strategic applications. Some legacy systems might stay on traditional infrastructure if modernization cost doesn't justify the benefit. Multi-cloud architecture might emerge for applications needing provider flexibility. Advanced optimization improves cost efficiency and performance.
Table 4: Phased Roadmap Timeline
Phase | Focus | Typical Duration | Team Size |
Phase 1 | Low-risk applications, capability building | 1-3 months | 3-5 engineers |
Phase 2 | Business-critical systems, full testing | 3-6 months | 5-8 engineers |
Phase 3 | Strategic applications, optimization | 6-12+ months | 4-10 engineers |
Resource numbers vary by organization size and application complexity. Estimates assume dedicated full-time staff; part-time allocation extends timelines proportionally.
Work can run in parallel once initial capability develops. Teams might begin Phase 2 planning while Phase 1 applications stabilize in production. Phase 3 testing environments get configured during Phase 2 execution. Some Phase 2 applications may require Phase 1 infrastructure changes to complete first. Dependency mapping from assessment guides this sequencing. Avoid spreading teams across too many concurrent efforts. Keep priorities clear.
Budget planning and cost control

The budget depends on modernization approach, application complexity, and team capability. Underestimating costs leads to difficult mid-project trade-offs.
Major cost categories
Migration expenses include tooling, consulting support, and dual-running periods when old and new systems operate simultaneously. Training develops team capabilities. Testing validates quality. Security implementation protects systems. Hidden costs emerge when productivity drops during learning curves. Support models require updates. Monitoring tools need expansion for distributed architectures. Egress fees accumulate when data transfers out of cloud environments. Cross-region data transfer adds costs in multi-region deployments.
Estimating budget
Replatforming costs less upfront than refactoring. Refactoring costs less than complete rearchitecting. Application count and complexity multiply baseline costs. Teams with existing cloud experience reduce external consulting needs. Calculate based on approach selection from previous decisions.
When costs exceed projections
Reassess scope before requesting additional budget. Some applications can wait. Others might work with simpler approaches. Budget ownership varies - some IT departments control spending, others need finance approval above certain thresholds. Clear ownership prevents delays when decisions need making.
Cost optimization and control
Start optimization during planning. Match infrastructure to actual requirements instead of overprovisioning. Automate shutdown of non-production environments. Use reserved capacity for predictable workloads. Set budget alerts early.
Monthly reviews compare actual to planned spending. Variance triggers investigation. Separate tracking for infrastructure, labor, licensing, and services provides visibility into where money goes.
Cloud provider managed services transfer operational burden - database administration, storage management, monitoring become their responsibility. This reduces staffing needs but creates dependencies.
Post-deployment optimization identifies unused resources and rightsizing opportunities. Tools like AWS Compute Optimizer and Azure Advisor analyze usage patterns and recommend instance size adjustments. Working with experienced teams reduces learning costs and avoids common mistakes. Cloud modernization services provide expertise when internal capability gaps exist.
Security and compliance considerations
Security mistakes during cloud modernization create expensive problems. Compliance violations bring fines and legal consequences. Data breaches damage reputation and customer trust.
Before you start
Identify which regulations apply. Healthcare organizations need HIPAA compliance for patient data. Financial services require SOC 2 and PCI-DSS. Government contractors face FedRAMP requirements. These mandates determine which cloud providers you can use and how you architect systems.
Assess current security gaps before migration. Document existing controls and known vulnerabilities. Some organizations discover compliance violations in legacy systems during this review. Fixing these before migration prevents transferring problems to cloud infrastructure.
Compliance requirements affect cloud provider selection. Not all providers support all compliance frameworks. AWS, Azure, and GCP each maintain different certifications. Multi-cloud environments increase complexity - each platform uses different identity and access management models, encryption key management systems, and security configuration interfaces.
Data sovereignty requirements for regulated industries often drive sovereign cloud adoption. Government agencies and healthcare providers in the EU may need to keep data within specific jurisdictions, using providers with regional data centers that guarantee physical location.
During migration
Data protection requires attention during transition. Encrypt data in transit between systems and at rest in storage. Classification drives protection levels - customer payment data needs stronger controls than product catalogs. Encryption-by-default policies reduce configuration errors.
Access control redesign happens during migration. Zero-trust architecture verifies requests based on identity, device status, and context rather than network location alone. While verifying every single request can introduce performance overhead in high-throughput systems, the approach significantly reduces attack surface for most applications.
Test security throughout each phase. Vulnerability scanning catches configuration mistakes before they reach production. Penetration testing validates controls. Compliance validation confirms regulatory requirements are met. Finding issues during testing costs less than fixing breaches after launch.
After deployment
Monitoring detects issues in production. Cloud provider security services integrate with internal tools. Automated alerts notify teams when suspicious activity appears. Response speed matters - automated containment reduces exposure compared to manual investigation.
Incident response plans account for cloud-specific scenarios. Compromised credentials, misconfigured storage buckets, and unauthorized API access require different responses than traditional infrastructure breaches. Practice procedures before incidents happen.
When to get help
Table 5: Security Expertise Requirements
Security Need | Internal Capability | External Support Recommended |
Basic compliance (HIPAA, PCI-DSS) | Sufficient with training | Review and validation |
Multi-cloud security architecture | Limited | Architecture design and implementation |
Zero-trust implementation | Varies | Design patterns and tool selection |
Regulated industries (FedRAMP, sovereign cloud) | Usually insufficient | Specialist involvement required |
Regulated industries benefit from specialist involvement. Compliance penalties exceed consulting costs. Multi-cloud architectures need expertise to maintain consistent security across platforms. Book a strategy session with our cloud experts to review security requirements before finalizing architecture.
FAQ
How long does cloud modernization strategy planning take?
Strategy development takes several weeks for most cases. This includes infrastructure assessment, approach selection, timeline development, and stakeholder alignment. Complex environments or strict compliance requirements extend planning timelines. Rushing this phase creates expensive corrections later when problems surface during execution.
Can existing teams handle cloud modernization or do we need new staff?
Existing teams typically handle modernization with training and temporary external support for specialized skills. New hires make sense when building permanent cloud capability matters long-term. Most companies use a hybrid approach - core team executes with external expertise filling capability gaps.
What's a realistic cloud modernization budget for mid-sized companies?
The budget depends on application count and modernization approach. Replatforming costs less than refactoring, which costs less than rearchitecting. Calculate based on approach selection from earlier decisions. Three applications cost less than thirty. Simple systems cost less than complex ones with extensive integrations.
Can cloud migration happen without business downtime?
Yes, through phased execution. Blue-green deployment maintains old systems while new ones get validated. Traffic gradually shifts after testing. Rollback capability provides quick recovery if issues appear. Some applications need brief maintenance windows for final cutover, but extended downtime isn't required.
How do we measure cloud modernization success?
Establish baselines before starting: deployment frequency, application response times, infrastructure costs, incident rates. Track these monthly. Success metrics vary by goals. Cost optimization projects track spending per transaction. Performance improvements measure response times. Development velocity projects measure time from code to production. Improvements become visible as modernized applications stabilize.
What are the biggest cloud modernization risks?
Underestimating complexity causes most failures. Teams discover unexpected dependencies between applications, which delays integration work. Data migration takes longer than planned when schema incompatibilities surface. Skills gaps slow execution across the project. Budget overruns eventually force scope cuts. Phased approaches manage these risks. Thorough assessment identifies blockers early. Realistic timelines account for learning curves.
Does multi-cloud strategy create vendor lock-in?
Provider-specific services create dependencies. AWS Lambda differs from Azure Functions, managed databases use different APIs, and data egress fees make moving large datasets expensive. Complete portability requires avoiding these services, which means managing more infrastructure and missing optimization opportunities. Companies typically accept some provider commitment for managed services that reduce operational overhead. Critical components benefit from abstraction layers. Data formats should remain portable to preserve flexibility.
Why do most companies use hybrid and multi-cloud architectures?
Hybrid architecture keeps sensitive data on-premises for regulatory compliance while using cloud for scalability. Multi-cloud prevents vendor lock-in and lets companies select best services from different providers. Data sovereignty requirements and latency optimization drive on-premises retention for specific workloads.
When should companies avoid cloud modernization?
Applications retiring within 18-24 months don't justify modernization investment. Stable systems meeting current needs without performance or scaling issues may work fine as-is. On-premises infrastructure often costs less for predictable workloads when hardware is already paid off, and legacy systems with unclear business value need evaluation before budget commitment.
Conclusion

Successful cloud modernization follows a clear sequence. Assessment reveals what you have and what needs changing. Choose the right approach for each application based on its requirements. Build a phased roadmap that starts with low-risk applications and progresses to business-critical systems. Budget realistically based on approach complexity and application count. Integrate security from the start, not after architecture decisions lock in.
These elements connect. Assessment findings inform approach selection. Approaches determine budget and timeline requirements. Phased execution builds team capability while managing risk. Security requirements influence provider selection and architecture patterns.
The professional services market for cloud modernization is projected to grow at a CAGR of 7.4% from 2025 to 2031 according to Intel Market Research, reflecting both project complexity and strong demand for expertise. Companies that combine internal knowledge with external support navigate this complexity faster and avoid costly mistakes. Start with infrastructure assessment.
When requirements exceed internal capability, contact Streamlogic to assess your infrastructure and build a phased modernization roadmap tailored to your business requirements.
References
IDC's Cloud Pulse Survey (Q3 2024) - Ten Trends That Shaped the Cloud Market in 2024, IDC Blog, February 2025
Cloud Modernization Services Market Growth Analysis, Dynamics, Key Players and Innovations, Outlook and Forecast 2025-2032, Intel Market Research, August 2025

Denis Avramenko
CTO, Co-Founder, Streamlogic


Technology Articles
Cloud Modernization Strategy Guide for Enterprises 2026
Dec 18, 2025


Technology Articles
How to Develop Cloud Applications: Complete Planning to Deployment Roadmap 2026
Dec 18, 2025


Technology Articles
Cloud Compliance in 2026: Navigating Standards, Strategies, and Best Practices
Dec 12, 2025


Technology Articles
Cloud Modernization Strategy Guide for Enterprises 2026
Dec 18, 2025


Technology Articles
How to Develop Cloud Applications: Complete Planning to Deployment Roadmap 2026
Dec 18, 2025


Technology Articles
Cloud Compliance in 2026: Navigating Standards, Strategies, and Best Practices
Dec 12, 2025
Reading time: 20 min
Before starting cloud modernization: assess your infrastructure, choose the right approach for each application, then build a phased roadmap with realistic budgets. Projects that skip this sequence hit budget overruns and extended timelines.
IDC's Cloud Pulse Survey (Q3 2024) found 82% of surveyed companies need cloud modernization, with 60% requiring major IT infrastructure transformation. The same research shows 88% use hybrid cloud and 79% multi-cloud environments for vendor flexibility and data sovereignty.
This guide covers infrastructure assessment, application-specific approaches, implementation sequencing, budget planning, and compliance frameworks.
Table of Contents
What cloud modernization means for your business
Migration vs modernization: making the right choice
What happens when you start without a strategy
Common mistakes when planning modernization
How to assess your current infrastructure
Choosing the right approach for each application
Building a phased roadmap that minimizes risk
Budget planning and cost control
Security and compliance considerations
What cloud modernization means for your business
Cloud modernization transforms legacy applications and infrastructure to run on modern cloud platforms. Migration moves existing systems to cloud infrastructure without architectural changes — the application runs on cloud servers instead of on-premises hardware, but the code and architecture stay the same. Modernization rebuilds applications to leverage cloud-native capabilities: automated scaling, managed databases, container orchestration, and distributed architectures.
Companies modernize to enable faster deployments and reduce operational overhead. System resilience improves when failures in one component don't cascade across the entire application. Monolithic applications get rearchitected into smaller components. Teams adopt container orchestration. Infrastructure automation replaces manual processes. These changes allow independent deployments rather than coordinated releases across entire systems.
Modernization introduces complexity. Distributed architectures need sophisticated monitoring across multiple components. Teams need expertise in container platforms and distributed system patterns. Network configuration becomes more involved. Moving from monolithic applications to microservices often reveals underestimated operational overhead when managing dozens or hundreds of services.
Hybrid and multi-cloud deployments have become the dominant model. Companies combine on-premises infrastructure with public cloud services to meet data sovereignty requirements and avoid vendor dependency. Cost optimization plays a role in platform selection. Some workloads remain on-premises due to regulatory constraints or latency requirements.
Table 1: What Changes During Modernization
Aspect | Before Modernization | After Modernization |
Deployment frequency | Weekly or monthly releases | Daily deployments possible |
Scaling | Manual capacity planning | Automated scaling for variable loads |
Infrastructure costs | Fixed capacity expenses | Usage-based pricing (with reserved capacity options for predictable workloads) |
Failure isolation | Single failure can affect entire system | Component failures contained to specific services |
Operational complexity | Centralized management | Distributed systems with multiple monitoring points |
Migration vs modernization: making the right choice
Cloud migration moves applications to cloud infrastructure without changing their architecture. Cloud modernization rebuilds the applications themselves to use cloud-native patterns and services.

Migration moves existing systems to new infrastructure. A financial processing system running on on-premises servers moves to cloud virtual machines. The application code, database schema, and integration points remain unchanged. Setup takes weeks because teams work with familiar architecture.
Modernization redesigns the application. The same financial system gets rebuilt with managed database services, event-driven processing, and automated scaling based on transaction volume. Teams can update the payment module without touching the reporting system.
When migration fits
Data center contracts expire within months
Budget covers infrastructure moves but not development work
Applications face retirement within two years
Teams lack cloud-native development expertise
Many companies migrate first to establish cloud operations expertise, then modernize applications based on business priority.
When modernization delivers value
Applications expected to run five years or longer
Current architecture can't handle doubled traffic
Business needs weekly releases instead of quarterly
Operational costs justify upfront investment
Modernization costs more upfront and requires more technical expertise. Applications built for cloud platforms often show lower operational costs over time.
Table 2: Migration vs Modernization
Factor | Migration | Modernization |
Code changes | Minimal configuration adjustments | Significant architectural redesign |
Timeline | Weeks to months depending on complexity | Months to over a year for complete transformation |
Cost structure | Lower initial investment | Higher upfront costs, potential long-term savings |
Risk level | Lower technical risk, familiar patterns | Higher risk, requires cloud-native expertise |
Reversibility | Straightforward to move back | Complex but possible with proper abstraction |
Best for | Short-term moves, budget constraints | Strategic applications, long-term operations |
Beyond these two options, approaches exist that combine migration with selective optimization. Hybrid architectures keep portions on-premises while moving others to cloud.
What happens when you start without a strategy

Projects without planning tend to hit the same problems. Industry data shows recognizable patterns when organizations skip strategy development.
Common challenges:
Budget overruns. Initial estimates often prove incorrect. Teams discover unexpected dependencies during execution. What seemed like a three-month project can extend to six or nine months, with corresponding cost increases.
Technical shortcuts accumulate. Deadline pressure leads to quick fixes that weren't meant to be permanent. Some get addressed later. Many don't. Each unresolved shortcut makes future changes harder.
Inconsistent security implementation. Without coordination, different teams apply different security standards. Some applications receive thorough hardening. Others get basic protection. The gaps usually surface during audits or when something breaks.
Higher team turnover. Extended timelines and constant firefighting affect morale. Some experienced engineers move to other opportunities. Knowledge transfer becomes a challenge when this happens.
Increased switching costs. Teams often choose services based on immediate fit rather than long-term flexibility. Over time, these choices can make changing providers expensive and complex.
Degraded system stability. As projects drag on without clear direction, maintenance windows grow longer. Performance issues become more frequent. User experience suffers, which stakeholders notice.
Fixing these issues mid-project costs more than preventing them. Projects often require pausing ongoing work, assessing what's accumulated, and adjusting course. A cloud modernization strategy helps by establishing priorities, realistic budgets, and coordination frameworks before work starts. Not every project without strategy fails, but the pattern appears often enough to merit attention.
Common mistakes when planning modernization
Mistake 1: Updating everything at once
The pressure for fast results pushes all applications into simultaneous modernization. Dependencies show up fast: Team A waits on Team B to finish database schema changes, Team C can't deploy until Team A completes. Nothing ships for months. Start with 2-3 applications and apply those learnings to the next batch.
Mistake 2: Assuming your current team has the skills
The assumption: existing team will figure out cloud-native architecture on the job. Reality: unfamiliar technologies slow everything down by 2-3x. What looked like cost savings from skipping training becomes project delays that cost far more. Plan 3-6 months for training or budget for external expertise before starting.
Mistake 3: Picking technology before understanding requirements
Without cloud skills, teams don't know how to evaluate requirements. So they choose what successful companies use - microservices, serverless, Kubernetes. Then discover the operational complexity doesn't fit a 4-person team. Managed Kubernetes services reduce some operational overhead, but still require expertise in container orchestration, networking, and distributed system patterns. Pick technology based on actual requirements and team capacity.
Mistake 4: Underestimating data migration
Data migration gets underestimated because it looks like a simple copy operation on paper. In practice, schemas need translation, data quality issues surface, and volume estimates prove optimistic. Migration tools like AWS Database Migration Service or Azure Data Migration Service handle technical transfer, but don't solve schema incompatibilities or data quality problems. Test data migration at production scale before the actual cutover, because discovering problems during go-live is expensive.
Mistake 5: Skipping success metrics
Success metrics get skipped in the rush to start. Nobody wants to slow down project kickoff with measurement discussions. Six months later, Engineering says performance improved while Finance says costs increased. Both are right because nobody defined what success meant upfront. Establish metrics before starting - deployment frequency, response times, costs - and track them monthly.
Mistake 6: Adding security and governance late
Security involvement gets delayed because architecture discussions feel like purely an engineering problem. When security finally reviews locked-in decisions, compliance violations require re-architecting core services. Months of delay, hundreds of thousands in rework. Involve security during initial architecture discussions when changes are still cheap.
Mistake 7: Skipping proper test environments
Production-equivalent environments have ongoing costs, so they get cut to save budget. Then production launch reveals what happens under real load: performance degrades, systems crash, customers can't access services. Emergency fixes cost 10x the monthly environment cost. Test at scale before launch, or pay significantly more fixing issues under customer pressure.
A cloud modernization strategy addresses these mistakes during planning when prevention costs less than recovery.
Table 2: Common Mistakes and Their Prevention
Mistake | Why It Happens | Real Consequence | Prevention |
Simultaneous modernization | Pressure for fast results | Teams blocked waiting on each other, nothing ships for months | Start with 2-3 apps, learn, then scale |
Skipped capability assessment | Assumption team will learn on the job | Tasks take 2-3x longer, project delays compound | 3-6 month training plan or external expertise |
Technology-first selection | No cloud skills to evaluate needs | Operational complexity team can't manage | Match technology to actual requirements and team size |
Data migration assumptions | Looks simple on paper | Schema issues, data quality failures at cutover | Test at production scale before go-live |
No success metrics | Rush to start without measurement discussions | Engineering vs Finance arguments with no data | Define and track metrics from day one |
Late security integration | Architecture feels like purely engineering problem | Re-architecture costs, months of delay | Security involved in initial architecture discussions |
Insufficient testing | Monthly environment costs seem expensive | Production failures, emergency fixes cost 10x more | Production-equivalent test environments |
How to assess your current infrastructure
Assessment tells you what you have before deciding what to change. Dependencies between applications get overlooked. External partner integrations get missed. Knowledge concentration risks stay invisible until someone leaves. Discovering these mid-project costs significantly more to fix.
Week 1: Critical minimum
Start with an application list. What runs the business, who owns it. Spreadsheet detail works here. Teams of 2-3 people working part-time can typically complete this for environments with 20-50 applications. Larger estates need more time or dedicated resources.
Data dependencies affect sequencing. App B pulls data from App A. Modernizing B requires A compatibility, though adapter layers provide temporary solutions. Map these flows now, or teams wait on blocked dependencies. Application performance monitoring tools automate dependency mapping, but manual validation catches what automation misses.
External integrations create business risk. Partner API integrations, vendor file transfers, third-party database connections - document these before changes begin. Breaking a partner's API during migration degrades their ability to send orders or process payments.
Knowledge concentration stays invisible until someone leaves or gets reassigned. Systems that only one person understands create operational risk. Flag these systems and plan knowledge transfer.
Compliance constraints come next. Healthcare data needs HIPAA. Payment processing needs PCI-DSS. These determine cloud provider selection. AWS supports FedRAMP for government workloads. Azure offers government cloud regions with specific compliance certifications. GCP provides assured workloads for regulated industries.
One week typically covers this minimum for smaller environments. Output enables application prioritization and identifies major blockers.
Weeks 2-4: Full picture
Extended assessment adds depth and requires dedicated resources or external help. Document current performance - response times, throughput, error rates. Without baselines, proving improvement becomes difficult.
Technical debt varies across applications. Some systems have solid code quality. Others have zero test coverage and documentation one person wrote years ago. Catalog what exists.
Infrastructure assets have financial implications. Servers, storage, networking equipment, licenses carry costs and depreciation schedules. For hybrid architectures, this inventory determines which workloads stay on-premises and which move to cloud based on regulatory requirements, latency needs, or cost optimization.
Full assessment takes 2-4 weeks with dedicated resources for organizations with 50-200 applications. Output is a structured report with application categories, dependency maps, cost analysis, and risk assessment.
What to do with results
Some applications work fine with minimal changes. Others need modernization to meet business goals. Some cost more to modernize than the benefit justifies.
Red flags need attention:
Critical (address before starting):
Compliance violations in current setup
Single points of failure that could stop revenue
Important (plan during assessment):
End-of-life software without replacement plans
Undocumented critical systems requiring knowledge transfer
Address critical red flags before starting modernization. If timeline pressure prevents completing full assessment, at minimum identify dependencies and compliance constraints before committing to delivery dates.
Choosing the right approach for each application
Choosing the right approach for each application
Three primary approaches handle most modernization scenarios. The decision depends on application characteristics, business requirements, team capability, and expected operational lifespan.
Replatforming: Minimal change, quick execution
Move applications to cloud infrastructure with minor configuration adjustments. Code and architecture remain largely unchanged. Works for applications on expensive infrastructure or systems with shorter lifespans. Implementation takes weeks to months. Struggles when performance improvements or architectural changes are needed.
Refactoring: Code optimization for cloud
Modify code to use cloud-native services while keeping overall architecture. Self-managed databases get replaced with managed services. Caching improves response times. Automated scaling handles variable loads. Implementation extends to months. Suits core applications with multi-year operational plans. Fails when fundamental architecture issues exist.
Rearchitecting: Complete transformation
Rebuild using cloud-native patterns where monoliths become microservices. Implementation measures in quarters. Targets strategic applications with 5+ year lifespans. Proves excessive for simple applications.
Example: Logistics tracking system
Replatforming moves servers and databases to cloud instances without code changes. Refactoring replaces the self-managed database with managed cloud services, implements caching for routes, and adds automated scaling. Rearchitecting breaks the monolith into independent services. Teams can update delivery notifications without touching route planning.
Table 3: Approach Selection Framework
Approach | Code Changes | Implementation Time | Works well for |
Replatforming | Minimal configuration | Weeks to months depending on complexity | Quick cloud presence, reduced infrastructure costs |
Refactoring | Moderate modifications | Months | Performance optimization, managed service adoption |
Rearchitecting | Complete redesign | Quarters to year+ | Strategic applications, fundamental capability changes |
The 7Rs framework (Rehost, Relocate, Replatform, Refactor, Repurchase, Retire, Retain) describes additional strategies. Retire eliminates applications no longer needed. Retain keeps workloads on-premises when regulatory requirements make cloud migration impractical.
Building a phased roadmap that minimizes risk
Phased implementation reduces risk by limiting what changes at once. Each phase builds capability needed for the next.

Phase 1: Quick wins (1-3 months)
Typically begin with 2-3 low-risk applications. Internal tools, development environments, or non-customer-facing applications work well. Teams gain initial cloud platform experience. The cloud migration strategy gets tested in practice. Stakeholders see progress. Document what works and what doesn't before moving forward.
Dependencies can extend Phase 1 timelines. An internal reporting tool that pulls data from customer-facing systems needs those integration points documented first. If Phase 1 reveals fundamental capability gaps or technical blockers, address these before touching business-critical systems. Advance to Phase 2 when teams demonstrate consistent execution and the approach proves viable.
Phase 2: Core systems (3-6 months)
Business-critical applications that need refactoring or rearchitecting legacy systems become the focus. Complexity increases, requiring more planning and testing. Performance testing happens at scale. Integration testing covers dependent systems.
Teams need established DevOps practices before Phase 2. Automated deployments reduce manual errors. Monitoring catches issues early. Incident response procedures ensure quick resolution. Without these foundations, risk increases significantly.
Phase 3: Complete transformation (6-12+ months)
This phase covers remaining strategic applications. Some legacy systems might stay on traditional infrastructure if modernization cost doesn't justify the benefit. Multi-cloud architecture might emerge for applications needing provider flexibility. Advanced optimization improves cost efficiency and performance.
Table 4: Phased Roadmap Timeline
Phase | Focus | Typical Duration | Team Size |
Phase 1 | Low-risk applications, capability building | 1-3 months | 3-5 engineers |
Phase 2 | Business-critical systems, full testing | 3-6 months | 5-8 engineers |
Phase 3 | Strategic applications, optimization | 6-12+ months | 4-10 engineers |
Resource numbers vary by organization size and application complexity. Estimates assume dedicated full-time staff; part-time allocation extends timelines proportionally.
Work can run in parallel once initial capability develops. Teams might begin Phase 2 planning while Phase 1 applications stabilize in production. Phase 3 testing environments get configured during Phase 2 execution. Some Phase 2 applications may require Phase 1 infrastructure changes to complete first. Dependency mapping from assessment guides this sequencing. Avoid spreading teams across too many concurrent efforts. Keep priorities clear.
Budget planning and cost control

The budget depends on modernization approach, application complexity, and team capability. Underestimating costs leads to difficult mid-project trade-offs.
Major cost categories
Migration expenses include tooling, consulting support, and dual-running periods when old and new systems operate simultaneously. Training develops team capabilities. Testing validates quality. Security implementation protects systems. Hidden costs emerge when productivity drops during learning curves. Support models require updates. Monitoring tools need expansion for distributed architectures. Egress fees accumulate when data transfers out of cloud environments. Cross-region data transfer adds costs in multi-region deployments.
Estimating budget
Replatforming costs less upfront than refactoring. Refactoring costs less than complete rearchitecting. Application count and complexity multiply baseline costs. Teams with existing cloud experience reduce external consulting needs. Calculate based on approach selection from previous decisions.
When costs exceed projections
Reassess scope before requesting additional budget. Some applications can wait. Others might work with simpler approaches. Budget ownership varies - some IT departments control spending, others need finance approval above certain thresholds. Clear ownership prevents delays when decisions need making.
Cost optimization and control
Start optimization during planning. Match infrastructure to actual requirements instead of overprovisioning. Automate shutdown of non-production environments. Use reserved capacity for predictable workloads. Set budget alerts early.
Monthly reviews compare actual to planned spending. Variance triggers investigation. Separate tracking for infrastructure, labor, licensing, and services provides visibility into where money goes.
Cloud provider managed services transfer operational burden - database administration, storage management, monitoring become their responsibility. This reduces staffing needs but creates dependencies.
Post-deployment optimization identifies unused resources and rightsizing opportunities. Tools like AWS Compute Optimizer and Azure Advisor analyze usage patterns and recommend instance size adjustments. Working with experienced teams reduces learning costs and avoids common mistakes. Cloud modernization services provide expertise when internal capability gaps exist.
Security and compliance considerations
Security mistakes during cloud modernization create expensive problems. Compliance violations bring fines and legal consequences. Data breaches damage reputation and customer trust.
Before you start
Identify which regulations apply. Healthcare organizations need HIPAA compliance for patient data. Financial services require SOC 2 and PCI-DSS. Government contractors face FedRAMP requirements. These mandates determine which cloud providers you can use and how you architect systems.
Assess current security gaps before migration. Document existing controls and known vulnerabilities. Some organizations discover compliance violations in legacy systems during this review. Fixing these before migration prevents transferring problems to cloud infrastructure.
Compliance requirements affect cloud provider selection. Not all providers support all compliance frameworks. AWS, Azure, and GCP each maintain different certifications. Multi-cloud environments increase complexity - each platform uses different identity and access management models, encryption key management systems, and security configuration interfaces.
Data sovereignty requirements for regulated industries often drive sovereign cloud adoption. Government agencies and healthcare providers in the EU may need to keep data within specific jurisdictions, using providers with regional data centers that guarantee physical location.
During migration
Data protection requires attention during transition. Encrypt data in transit between systems and at rest in storage. Classification drives protection levels - customer payment data needs stronger controls than product catalogs. Encryption-by-default policies reduce configuration errors.
Access control redesign happens during migration. Zero-trust architecture verifies requests based on identity, device status, and context rather than network location alone. While verifying every single request can introduce performance overhead in high-throughput systems, the approach significantly reduces attack surface for most applications.
Test security throughout each phase. Vulnerability scanning catches configuration mistakes before they reach production. Penetration testing validates controls. Compliance validation confirms regulatory requirements are met. Finding issues during testing costs less than fixing breaches after launch.
After deployment
Monitoring detects issues in production. Cloud provider security services integrate with internal tools. Automated alerts notify teams when suspicious activity appears. Response speed matters - automated containment reduces exposure compared to manual investigation.
Incident response plans account for cloud-specific scenarios. Compromised credentials, misconfigured storage buckets, and unauthorized API access require different responses than traditional infrastructure breaches. Practice procedures before incidents happen.
When to get help
Table 5: Security Expertise Requirements
Security Need | Internal Capability | External Support Recommended |
Basic compliance (HIPAA, PCI-DSS) | Sufficient with training | Review and validation |
Multi-cloud security architecture | Limited | Architecture design and implementation |
Zero-trust implementation | Varies | Design patterns and tool selection |
Regulated industries (FedRAMP, sovereign cloud) | Usually insufficient | Specialist involvement required |
Regulated industries benefit from specialist involvement. Compliance penalties exceed consulting costs. Multi-cloud architectures need expertise to maintain consistent security across platforms. Book a strategy session with our cloud experts to review security requirements before finalizing architecture.
FAQ
How long does cloud modernization strategy planning take?
Strategy development takes several weeks for most cases. This includes infrastructure assessment, approach selection, timeline development, and stakeholder alignment. Complex environments or strict compliance requirements extend planning timelines. Rushing this phase creates expensive corrections later when problems surface during execution.
Can existing teams handle cloud modernization or do we need new staff?
Existing teams typically handle modernization with training and temporary external support for specialized skills. New hires make sense when building permanent cloud capability matters long-term. Most companies use a hybrid approach - core team executes with external expertise filling capability gaps.
What's a realistic cloud modernization budget for mid-sized companies?
The budget depends on application count and modernization approach. Replatforming costs less than refactoring, which costs less than rearchitecting. Calculate based on approach selection from earlier decisions. Three applications cost less than thirty. Simple systems cost less than complex ones with extensive integrations.
Can cloud migration happen without business downtime?
Yes, through phased execution. Blue-green deployment maintains old systems while new ones get validated. Traffic gradually shifts after testing. Rollback capability provides quick recovery if issues appear. Some applications need brief maintenance windows for final cutover, but extended downtime isn't required.
How do we measure cloud modernization success?
Establish baselines before starting: deployment frequency, application response times, infrastructure costs, incident rates. Track these monthly. Success metrics vary by goals. Cost optimization projects track spending per transaction. Performance improvements measure response times. Development velocity projects measure time from code to production. Improvements become visible as modernized applications stabilize.
What are the biggest cloud modernization risks?
Underestimating complexity causes most failures. Teams discover unexpected dependencies between applications, which delays integration work. Data migration takes longer than planned when schema incompatibilities surface. Skills gaps slow execution across the project. Budget overruns eventually force scope cuts. Phased approaches manage these risks. Thorough assessment identifies blockers early. Realistic timelines account for learning curves.
Does multi-cloud strategy create vendor lock-in?
Provider-specific services create dependencies. AWS Lambda differs from Azure Functions, managed databases use different APIs, and data egress fees make moving large datasets expensive. Complete portability requires avoiding these services, which means managing more infrastructure and missing optimization opportunities. Companies typically accept some provider commitment for managed services that reduce operational overhead. Critical components benefit from abstraction layers. Data formats should remain portable to preserve flexibility.
Why do most companies use hybrid and multi-cloud architectures?
Hybrid architecture keeps sensitive data on-premises for regulatory compliance while using cloud for scalability. Multi-cloud prevents vendor lock-in and lets companies select best services from different providers. Data sovereignty requirements and latency optimization drive on-premises retention for specific workloads.
When should companies avoid cloud modernization?
Applications retiring within 18-24 months don't justify modernization investment. Stable systems meeting current needs without performance or scaling issues may work fine as-is. On-premises infrastructure often costs less for predictable workloads when hardware is already paid off, and legacy systems with unclear business value need evaluation before budget commitment.
Conclusion

Successful cloud modernization follows a clear sequence. Assessment reveals what you have and what needs changing. Choose the right approach for each application based on its requirements. Build a phased roadmap that starts with low-risk applications and progresses to business-critical systems. Budget realistically based on approach complexity and application count. Integrate security from the start, not after architecture decisions lock in.
These elements connect. Assessment findings inform approach selection. Approaches determine budget and timeline requirements. Phased execution builds team capability while managing risk. Security requirements influence provider selection and architecture patterns.
The professional services market for cloud modernization is projected to grow at a CAGR of 7.4% from 2025 to 2031 according to Intel Market Research, reflecting both project complexity and strong demand for expertise. Companies that combine internal knowledge with external support navigate this complexity faster and avoid costly mistakes. Start with infrastructure assessment.
When requirements exceed internal capability, contact Streamlogic to assess your infrastructure and build a phased modernization roadmap tailored to your business requirements.
References
IDC's Cloud Pulse Survey (Q3 2024) - Ten Trends That Shaped the Cloud Market in 2024, IDC Blog, February 2025
Cloud Modernization Services Market Growth Analysis, Dynamics, Key Players and Innovations, Outlook and Forecast 2025-2032, Intel Market Research, August 2025

Denis Avramenko
CTO, Co-Founder, Streamlogic
Reading time: 20 min
Before starting cloud modernization: assess your infrastructure, choose the right approach for each application, then build a phased roadmap with realistic budgets. Projects that skip this sequence hit budget overruns and extended timelines.
IDC's Cloud Pulse Survey (Q3 2024) found 82% of surveyed companies need cloud modernization, with 60% requiring major IT infrastructure transformation. The same research shows 88% use hybrid cloud and 79% multi-cloud environments for vendor flexibility and data sovereignty.
This guide covers infrastructure assessment, application-specific approaches, implementation sequencing, budget planning, and compliance frameworks.
Table of Contents
What cloud modernization means for your business
Migration vs modernization: making the right choice
What happens when you start without a strategy
Common mistakes when planning modernization
How to assess your current infrastructure
Choosing the right approach for each application
Building a phased roadmap that minimizes risk
Budget planning and cost control
Security and compliance considerations
What cloud modernization means for your business
Cloud modernization transforms legacy applications and infrastructure to run on modern cloud platforms. Migration moves existing systems to cloud infrastructure without architectural changes — the application runs on cloud servers instead of on-premises hardware, but the code and architecture stay the same. Modernization rebuilds applications to leverage cloud-native capabilities: automated scaling, managed databases, container orchestration, and distributed architectures.
Companies modernize to enable faster deployments and reduce operational overhead. System resilience improves when failures in one component don't cascade across the entire application. Monolithic applications get rearchitected into smaller components. Teams adopt container orchestration. Infrastructure automation replaces manual processes. These changes allow independent deployments rather than coordinated releases across entire systems.
Modernization introduces complexity. Distributed architectures need sophisticated monitoring across multiple components. Teams need expertise in container platforms and distributed system patterns. Network configuration becomes more involved. Moving from monolithic applications to microservices often reveals underestimated operational overhead when managing dozens or hundreds of services.
Hybrid and multi-cloud deployments have become the dominant model. Companies combine on-premises infrastructure with public cloud services to meet data sovereignty requirements and avoid vendor dependency. Cost optimization plays a role in platform selection. Some workloads remain on-premises due to regulatory constraints or latency requirements.
Table 1: What Changes During Modernization
Aspect | Before Modernization | After Modernization |
Deployment frequency | Weekly or monthly releases | Daily deployments possible |
Scaling | Manual capacity planning | Automated scaling for variable loads |
Infrastructure costs | Fixed capacity expenses | Usage-based pricing (with reserved capacity options for predictable workloads) |
Failure isolation | Single failure can affect entire system | Component failures contained to specific services |
Operational complexity | Centralized management | Distributed systems with multiple monitoring points |
Migration vs modernization: making the right choice
Cloud migration moves applications to cloud infrastructure without changing their architecture. Cloud modernization rebuilds the applications themselves to use cloud-native patterns and services.

Migration moves existing systems to new infrastructure. A financial processing system running on on-premises servers moves to cloud virtual machines. The application code, database schema, and integration points remain unchanged. Setup takes weeks because teams work with familiar architecture.
Modernization redesigns the application. The same financial system gets rebuilt with managed database services, event-driven processing, and automated scaling based on transaction volume. Teams can update the payment module without touching the reporting system.
When migration fits
Data center contracts expire within months
Budget covers infrastructure moves but not development work
Applications face retirement within two years
Teams lack cloud-native development expertise
Many companies migrate first to establish cloud operations expertise, then modernize applications based on business priority.
When modernization delivers value
Applications expected to run five years or longer
Current architecture can't handle doubled traffic
Business needs weekly releases instead of quarterly
Operational costs justify upfront investment
Modernization costs more upfront and requires more technical expertise. Applications built for cloud platforms often show lower operational costs over time.
Table 2: Migration vs Modernization
Factor | Migration | Modernization |
Code changes | Minimal configuration adjustments | Significant architectural redesign |
Timeline | Weeks to months depending on complexity | Months to over a year for complete transformation |
Cost structure | Lower initial investment | Higher upfront costs, potential long-term savings |
Risk level | Lower technical risk, familiar patterns | Higher risk, requires cloud-native expertise |
Reversibility | Straightforward to move back | Complex but possible with proper abstraction |
Best for | Short-term moves, budget constraints | Strategic applications, long-term operations |
Beyond these two options, approaches exist that combine migration with selective optimization. Hybrid architectures keep portions on-premises while moving others to cloud.
What happens when you start without a strategy

Projects without planning tend to hit the same problems. Industry data shows recognizable patterns when organizations skip strategy development.
Common challenges:
Budget overruns. Initial estimates often prove incorrect. Teams discover unexpected dependencies during execution. What seemed like a three-month project can extend to six or nine months, with corresponding cost increases.
Technical shortcuts accumulate. Deadline pressure leads to quick fixes that weren't meant to be permanent. Some get addressed later. Many don't. Each unresolved shortcut makes future changes harder.
Inconsistent security implementation. Without coordination, different teams apply different security standards. Some applications receive thorough hardening. Others get basic protection. The gaps usually surface during audits or when something breaks.
Higher team turnover. Extended timelines and constant firefighting affect morale. Some experienced engineers move to other opportunities. Knowledge transfer becomes a challenge when this happens.
Increased switching costs. Teams often choose services based on immediate fit rather than long-term flexibility. Over time, these choices can make changing providers expensive and complex.
Degraded system stability. As projects drag on without clear direction, maintenance windows grow longer. Performance issues become more frequent. User experience suffers, which stakeholders notice.
Fixing these issues mid-project costs more than preventing them. Projects often require pausing ongoing work, assessing what's accumulated, and adjusting course. A cloud modernization strategy helps by establishing priorities, realistic budgets, and coordination frameworks before work starts. Not every project without strategy fails, but the pattern appears often enough to merit attention.
Common mistakes when planning modernization
Mistake 1: Updating everything at once
The pressure for fast results pushes all applications into simultaneous modernization. Dependencies show up fast: Team A waits on Team B to finish database schema changes, Team C can't deploy until Team A completes. Nothing ships for months. Start with 2-3 applications and apply those learnings to the next batch.
Mistake 2: Assuming your current team has the skills
The assumption: existing team will figure out cloud-native architecture on the job. Reality: unfamiliar technologies slow everything down by 2-3x. What looked like cost savings from skipping training becomes project delays that cost far more. Plan 3-6 months for training or budget for external expertise before starting.
Mistake 3: Picking technology before understanding requirements
Without cloud skills, teams don't know how to evaluate requirements. So they choose what successful companies use - microservices, serverless, Kubernetes. Then discover the operational complexity doesn't fit a 4-person team. Managed Kubernetes services reduce some operational overhead, but still require expertise in container orchestration, networking, and distributed system patterns. Pick technology based on actual requirements and team capacity.
Mistake 4: Underestimating data migration
Data migration gets underestimated because it looks like a simple copy operation on paper. In practice, schemas need translation, data quality issues surface, and volume estimates prove optimistic. Migration tools like AWS Database Migration Service or Azure Data Migration Service handle technical transfer, but don't solve schema incompatibilities or data quality problems. Test data migration at production scale before the actual cutover, because discovering problems during go-live is expensive.
Mistake 5: Skipping success metrics
Success metrics get skipped in the rush to start. Nobody wants to slow down project kickoff with measurement discussions. Six months later, Engineering says performance improved while Finance says costs increased. Both are right because nobody defined what success meant upfront. Establish metrics before starting - deployment frequency, response times, costs - and track them monthly.
Mistake 6: Adding security and governance late
Security involvement gets delayed because architecture discussions feel like purely an engineering problem. When security finally reviews locked-in decisions, compliance violations require re-architecting core services. Months of delay, hundreds of thousands in rework. Involve security during initial architecture discussions when changes are still cheap.
Mistake 7: Skipping proper test environments
Production-equivalent environments have ongoing costs, so they get cut to save budget. Then production launch reveals what happens under real load: performance degrades, systems crash, customers can't access services. Emergency fixes cost 10x the monthly environment cost. Test at scale before launch, or pay significantly more fixing issues under customer pressure.
A cloud modernization strategy addresses these mistakes during planning when prevention costs less than recovery.
Table 2: Common Mistakes and Their Prevention
Mistake | Why It Happens | Real Consequence | Prevention |
Simultaneous modernization | Pressure for fast results | Teams blocked waiting on each other, nothing ships for months | Start with 2-3 apps, learn, then scale |
Skipped capability assessment | Assumption team will learn on the job | Tasks take 2-3x longer, project delays compound | 3-6 month training plan or external expertise |
Technology-first selection | No cloud skills to evaluate needs | Operational complexity team can't manage | Match technology to actual requirements and team size |
Data migration assumptions | Looks simple on paper | Schema issues, data quality failures at cutover | Test at production scale before go-live |
No success metrics | Rush to start without measurement discussions | Engineering vs Finance arguments with no data | Define and track metrics from day one |
Late security integration | Architecture feels like purely engineering problem | Re-architecture costs, months of delay | Security involved in initial architecture discussions |
Insufficient testing | Monthly environment costs seem expensive | Production failures, emergency fixes cost 10x more | Production-equivalent test environments |
How to assess your current infrastructure
Assessment tells you what you have before deciding what to change. Dependencies between applications get overlooked. External partner integrations get missed. Knowledge concentration risks stay invisible until someone leaves. Discovering these mid-project costs significantly more to fix.
Week 1: Critical minimum
Start with an application list. What runs the business, who owns it. Spreadsheet detail works here. Teams of 2-3 people working part-time can typically complete this for environments with 20-50 applications. Larger estates need more time or dedicated resources.
Data dependencies affect sequencing. App B pulls data from App A. Modernizing B requires A compatibility, though adapter layers provide temporary solutions. Map these flows now, or teams wait on blocked dependencies. Application performance monitoring tools automate dependency mapping, but manual validation catches what automation misses.
External integrations create business risk. Partner API integrations, vendor file transfers, third-party database connections - document these before changes begin. Breaking a partner's API during migration degrades their ability to send orders or process payments.
Knowledge concentration stays invisible until someone leaves or gets reassigned. Systems that only one person understands create operational risk. Flag these systems and plan knowledge transfer.
Compliance constraints come next. Healthcare data needs HIPAA. Payment processing needs PCI-DSS. These determine cloud provider selection. AWS supports FedRAMP for government workloads. Azure offers government cloud regions with specific compliance certifications. GCP provides assured workloads for regulated industries.
One week typically covers this minimum for smaller environments. Output enables application prioritization and identifies major blockers.
Weeks 2-4: Full picture
Extended assessment adds depth and requires dedicated resources or external help. Document current performance - response times, throughput, error rates. Without baselines, proving improvement becomes difficult.
Technical debt varies across applications. Some systems have solid code quality. Others have zero test coverage and documentation one person wrote years ago. Catalog what exists.
Infrastructure assets have financial implications. Servers, storage, networking equipment, licenses carry costs and depreciation schedules. For hybrid architectures, this inventory determines which workloads stay on-premises and which move to cloud based on regulatory requirements, latency needs, or cost optimization.
Full assessment takes 2-4 weeks with dedicated resources for organizations with 50-200 applications. Output is a structured report with application categories, dependency maps, cost analysis, and risk assessment.
What to do with results
Some applications work fine with minimal changes. Others need modernization to meet business goals. Some cost more to modernize than the benefit justifies.
Red flags need attention:
Critical (address before starting):
Compliance violations in current setup
Single points of failure that could stop revenue
Important (plan during assessment):
End-of-life software without replacement plans
Undocumented critical systems requiring knowledge transfer
Address critical red flags before starting modernization. If timeline pressure prevents completing full assessment, at minimum identify dependencies and compliance constraints before committing to delivery dates.
Choosing the right approach for each application
Choosing the right approach for each application
Three primary approaches handle most modernization scenarios. The decision depends on application characteristics, business requirements, team capability, and expected operational lifespan.
Replatforming: Minimal change, quick execution
Move applications to cloud infrastructure with minor configuration adjustments. Code and architecture remain largely unchanged. Works for applications on expensive infrastructure or systems with shorter lifespans. Implementation takes weeks to months. Struggles when performance improvements or architectural changes are needed.
Refactoring: Code optimization for cloud
Modify code to use cloud-native services while keeping overall architecture. Self-managed databases get replaced with managed services. Caching improves response times. Automated scaling handles variable loads. Implementation extends to months. Suits core applications with multi-year operational plans. Fails when fundamental architecture issues exist.
Rearchitecting: Complete transformation
Rebuild using cloud-native patterns where monoliths become microservices. Implementation measures in quarters. Targets strategic applications with 5+ year lifespans. Proves excessive for simple applications.
Example: Logistics tracking system
Replatforming moves servers and databases to cloud instances without code changes. Refactoring replaces the self-managed database with managed cloud services, implements caching for routes, and adds automated scaling. Rearchitecting breaks the monolith into independent services. Teams can update delivery notifications without touching route planning.
Table 3: Approach Selection Framework
Approach | Code Changes | Implementation Time | Works well for |
Replatforming | Minimal configuration | Weeks to months depending on complexity | Quick cloud presence, reduced infrastructure costs |
Refactoring | Moderate modifications | Months | Performance optimization, managed service adoption |
Rearchitecting | Complete redesign | Quarters to year+ | Strategic applications, fundamental capability changes |
The 7Rs framework (Rehost, Relocate, Replatform, Refactor, Repurchase, Retire, Retain) describes additional strategies. Retire eliminates applications no longer needed. Retain keeps workloads on-premises when regulatory requirements make cloud migration impractical.
Building a phased roadmap that minimizes risk
Phased implementation reduces risk by limiting what changes at once. Each phase builds capability needed for the next.

Phase 1: Quick wins (1-3 months)
Typically begin with 2-3 low-risk applications. Internal tools, development environments, or non-customer-facing applications work well. Teams gain initial cloud platform experience. The cloud migration strategy gets tested in practice. Stakeholders see progress. Document what works and what doesn't before moving forward.
Dependencies can extend Phase 1 timelines. An internal reporting tool that pulls data from customer-facing systems needs those integration points documented first. If Phase 1 reveals fundamental capability gaps or technical blockers, address these before touching business-critical systems. Advance to Phase 2 when teams demonstrate consistent execution and the approach proves viable.
Phase 2: Core systems (3-6 months)
Business-critical applications that need refactoring or rearchitecting legacy systems become the focus. Complexity increases, requiring more planning and testing. Performance testing happens at scale. Integration testing covers dependent systems.
Teams need established DevOps practices before Phase 2. Automated deployments reduce manual errors. Monitoring catches issues early. Incident response procedures ensure quick resolution. Without these foundations, risk increases significantly.
Phase 3: Complete transformation (6-12+ months)
This phase covers remaining strategic applications. Some legacy systems might stay on traditional infrastructure if modernization cost doesn't justify the benefit. Multi-cloud architecture might emerge for applications needing provider flexibility. Advanced optimization improves cost efficiency and performance.
Table 4: Phased Roadmap Timeline
Phase | Focus | Typical Duration | Team Size |
Phase 1 | Low-risk applications, capability building | 1-3 months | 3-5 engineers |
Phase 2 | Business-critical systems, full testing | 3-6 months | 5-8 engineers |
Phase 3 | Strategic applications, optimization | 6-12+ months | 4-10 engineers |
Resource numbers vary by organization size and application complexity. Estimates assume dedicated full-time staff; part-time allocation extends timelines proportionally.
Work can run in parallel once initial capability develops. Teams might begin Phase 2 planning while Phase 1 applications stabilize in production. Phase 3 testing environments get configured during Phase 2 execution. Some Phase 2 applications may require Phase 1 infrastructure changes to complete first. Dependency mapping from assessment guides this sequencing. Avoid spreading teams across too many concurrent efforts. Keep priorities clear.
Budget planning and cost control

The budget depends on modernization approach, application complexity, and team capability. Underestimating costs leads to difficult mid-project trade-offs.
Major cost categories
Migration expenses include tooling, consulting support, and dual-running periods when old and new systems operate simultaneously. Training develops team capabilities. Testing validates quality. Security implementation protects systems. Hidden costs emerge when productivity drops during learning curves. Support models require updates. Monitoring tools need expansion for distributed architectures. Egress fees accumulate when data transfers out of cloud environments. Cross-region data transfer adds costs in multi-region deployments.
Estimating budget
Replatforming costs less upfront than refactoring. Refactoring costs less than complete rearchitecting. Application count and complexity multiply baseline costs. Teams with existing cloud experience reduce external consulting needs. Calculate based on approach selection from previous decisions.
When costs exceed projections
Reassess scope before requesting additional budget. Some applications can wait. Others might work with simpler approaches. Budget ownership varies - some IT departments control spending, others need finance approval above certain thresholds. Clear ownership prevents delays when decisions need making.
Cost optimization and control
Start optimization during planning. Match infrastructure to actual requirements instead of overprovisioning. Automate shutdown of non-production environments. Use reserved capacity for predictable workloads. Set budget alerts early.
Monthly reviews compare actual to planned spending. Variance triggers investigation. Separate tracking for infrastructure, labor, licensing, and services provides visibility into where money goes.
Cloud provider managed services transfer operational burden - database administration, storage management, monitoring become their responsibility. This reduces staffing needs but creates dependencies.
Post-deployment optimization identifies unused resources and rightsizing opportunities. Tools like AWS Compute Optimizer and Azure Advisor analyze usage patterns and recommend instance size adjustments. Working with experienced teams reduces learning costs and avoids common mistakes. Cloud modernization services provide expertise when internal capability gaps exist.
Security and compliance considerations
Security mistakes during cloud modernization create expensive problems. Compliance violations bring fines and legal consequences. Data breaches damage reputation and customer trust.
Before you start
Identify which regulations apply. Healthcare organizations need HIPAA compliance for patient data. Financial services require SOC 2 and PCI-DSS. Government contractors face FedRAMP requirements. These mandates determine which cloud providers you can use and how you architect systems.
Assess current security gaps before migration. Document existing controls and known vulnerabilities. Some organizations discover compliance violations in legacy systems during this review. Fixing these before migration prevents transferring problems to cloud infrastructure.
Compliance requirements affect cloud provider selection. Not all providers support all compliance frameworks. AWS, Azure, and GCP each maintain different certifications. Multi-cloud environments increase complexity - each platform uses different identity and access management models, encryption key management systems, and security configuration interfaces.
Data sovereignty requirements for regulated industries often drive sovereign cloud adoption. Government agencies and healthcare providers in the EU may need to keep data within specific jurisdictions, using providers with regional data centers that guarantee physical location.
During migration
Data protection requires attention during transition. Encrypt data in transit between systems and at rest in storage. Classification drives protection levels - customer payment data needs stronger controls than product catalogs. Encryption-by-default policies reduce configuration errors.
Access control redesign happens during migration. Zero-trust architecture verifies requests based on identity, device status, and context rather than network location alone. While verifying every single request can introduce performance overhead in high-throughput systems, the approach significantly reduces attack surface for most applications.
Test security throughout each phase. Vulnerability scanning catches configuration mistakes before they reach production. Penetration testing validates controls. Compliance validation confirms regulatory requirements are met. Finding issues during testing costs less than fixing breaches after launch.
After deployment
Monitoring detects issues in production. Cloud provider security services integrate with internal tools. Automated alerts notify teams when suspicious activity appears. Response speed matters - automated containment reduces exposure compared to manual investigation.
Incident response plans account for cloud-specific scenarios. Compromised credentials, misconfigured storage buckets, and unauthorized API access require different responses than traditional infrastructure breaches. Practice procedures before incidents happen.
When to get help
Table 5: Security Expertise Requirements
Security Need | Internal Capability | External Support Recommended |
Basic compliance (HIPAA, PCI-DSS) | Sufficient with training | Review and validation |
Multi-cloud security architecture | Limited | Architecture design and implementation |
Zero-trust implementation | Varies | Design patterns and tool selection |
Regulated industries (FedRAMP, sovereign cloud) | Usually insufficient | Specialist involvement required |
Regulated industries benefit from specialist involvement. Compliance penalties exceed consulting costs. Multi-cloud architectures need expertise to maintain consistent security across platforms. Book a strategy session with our cloud experts to review security requirements before finalizing architecture.
FAQ
How long does cloud modernization strategy planning take?
Strategy development takes several weeks for most cases. This includes infrastructure assessment, approach selection, timeline development, and stakeholder alignment. Complex environments or strict compliance requirements extend planning timelines. Rushing this phase creates expensive corrections later when problems surface during execution.
Can existing teams handle cloud modernization or do we need new staff?
Existing teams typically handle modernization with training and temporary external support for specialized skills. New hires make sense when building permanent cloud capability matters long-term. Most companies use a hybrid approach - core team executes with external expertise filling capability gaps.
What's a realistic cloud modernization budget for mid-sized companies?
The budget depends on application count and modernization approach. Replatforming costs less than refactoring, which costs less than rearchitecting. Calculate based on approach selection from earlier decisions. Three applications cost less than thirty. Simple systems cost less than complex ones with extensive integrations.
Can cloud migration happen without business downtime?
Yes, through phased execution. Blue-green deployment maintains old systems while new ones get validated. Traffic gradually shifts after testing. Rollback capability provides quick recovery if issues appear. Some applications need brief maintenance windows for final cutover, but extended downtime isn't required.
How do we measure cloud modernization success?
Establish baselines before starting: deployment frequency, application response times, infrastructure costs, incident rates. Track these monthly. Success metrics vary by goals. Cost optimization projects track spending per transaction. Performance improvements measure response times. Development velocity projects measure time from code to production. Improvements become visible as modernized applications stabilize.
What are the biggest cloud modernization risks?
Underestimating complexity causes most failures. Teams discover unexpected dependencies between applications, which delays integration work. Data migration takes longer than planned when schema incompatibilities surface. Skills gaps slow execution across the project. Budget overruns eventually force scope cuts. Phased approaches manage these risks. Thorough assessment identifies blockers early. Realistic timelines account for learning curves.
Does multi-cloud strategy create vendor lock-in?
Provider-specific services create dependencies. AWS Lambda differs from Azure Functions, managed databases use different APIs, and data egress fees make moving large datasets expensive. Complete portability requires avoiding these services, which means managing more infrastructure and missing optimization opportunities. Companies typically accept some provider commitment for managed services that reduce operational overhead. Critical components benefit from abstraction layers. Data formats should remain portable to preserve flexibility.
Why do most companies use hybrid and multi-cloud architectures?
Hybrid architecture keeps sensitive data on-premises for regulatory compliance while using cloud for scalability. Multi-cloud prevents vendor lock-in and lets companies select best services from different providers. Data sovereignty requirements and latency optimization drive on-premises retention for specific workloads.
When should companies avoid cloud modernization?
Applications retiring within 18-24 months don't justify modernization investment. Stable systems meeting current needs without performance or scaling issues may work fine as-is. On-premises infrastructure often costs less for predictable workloads when hardware is already paid off, and legacy systems with unclear business value need evaluation before budget commitment.
Conclusion

Successful cloud modernization follows a clear sequence. Assessment reveals what you have and what needs changing. Choose the right approach for each application based on its requirements. Build a phased roadmap that starts with low-risk applications and progresses to business-critical systems. Budget realistically based on approach complexity and application count. Integrate security from the start, not after architecture decisions lock in.
These elements connect. Assessment findings inform approach selection. Approaches determine budget and timeline requirements. Phased execution builds team capability while managing risk. Security requirements influence provider selection and architecture patterns.
The professional services market for cloud modernization is projected to grow at a CAGR of 7.4% from 2025 to 2031 according to Intel Market Research, reflecting both project complexity and strong demand for expertise. Companies that combine internal knowledge with external support navigate this complexity faster and avoid costly mistakes. Start with infrastructure assessment.
When requirements exceed internal capability, contact Streamlogic to assess your infrastructure and build a phased modernization roadmap tailored to your business requirements.
References
IDC's Cloud Pulse Survey (Q3 2024) - Ten Trends That Shaped the Cloud Market in 2024, IDC Blog, February 2025
Cloud Modernization Services Market Growth Analysis, Dynamics, Key Players and Innovations, Outlook and Forecast 2025-2032, Intel Market Research, August 2025

Denis Avramenko
CTO, Co-Founder, Streamlogic


Technology Articles
Cloud Modernization Strategy Guide for Enterprises 2026
Dec 18, 2025


Technology Articles
How to Develop Cloud Applications: Complete Planning to Deployment Roadmap 2026
Dec 18, 2025


Technology Articles
Cloud Compliance in 2026: Navigating Standards, Strategies, and Best Practices
Dec 12, 2025
Tech Council
Technology Articles
Cloud Modernization Strategy Guide for Enterprises 2026
Avoid costly mistakes in cloud modernization. Learn planning best practices, how strategy optimizes budget, and practical steps to reduce risks.

Denis Avramenko
CTO, Co-Founder, Streamlogic
Dec 18, 2025

