Tech Council
Technology Articles
Cloud Compliance in 2026: Navigating Standards, Strategies, and Best Practices
Learn regulatory frameworks, shared responsibility model, audit methodology, and multi-cloud security challenges. Breach cost data and 2026 trend analysis.

Denis Avramenko
CTO, Co-Founder, Streamlogic
Dec 12, 2025

Table of Contents
Key insights: cloud compliance in 2026
What is cloud compliance and why is it critical in 2026?
The cost of non-compliance in cloud environments
Essential cloud compliance standards and regulations you need to know
Main cloud compliance challenges organizations face today
How does the shared responsibility model work in cloud compliance?
Implementing effective cloud governance in your organization
What best practices ensure cloud compliance and data security?
Steps to audit your cloud environment for compliance
How is cloud compliance evolving: what to expect in 2026 and beyond?
Key insights: cloud compliance in 2026
Companies face mounting pressure to demonstrate their cloud infrastructure meets security and privacy requirements, as customers increasingly require proof of regulatory adherence before finalizing agreements.
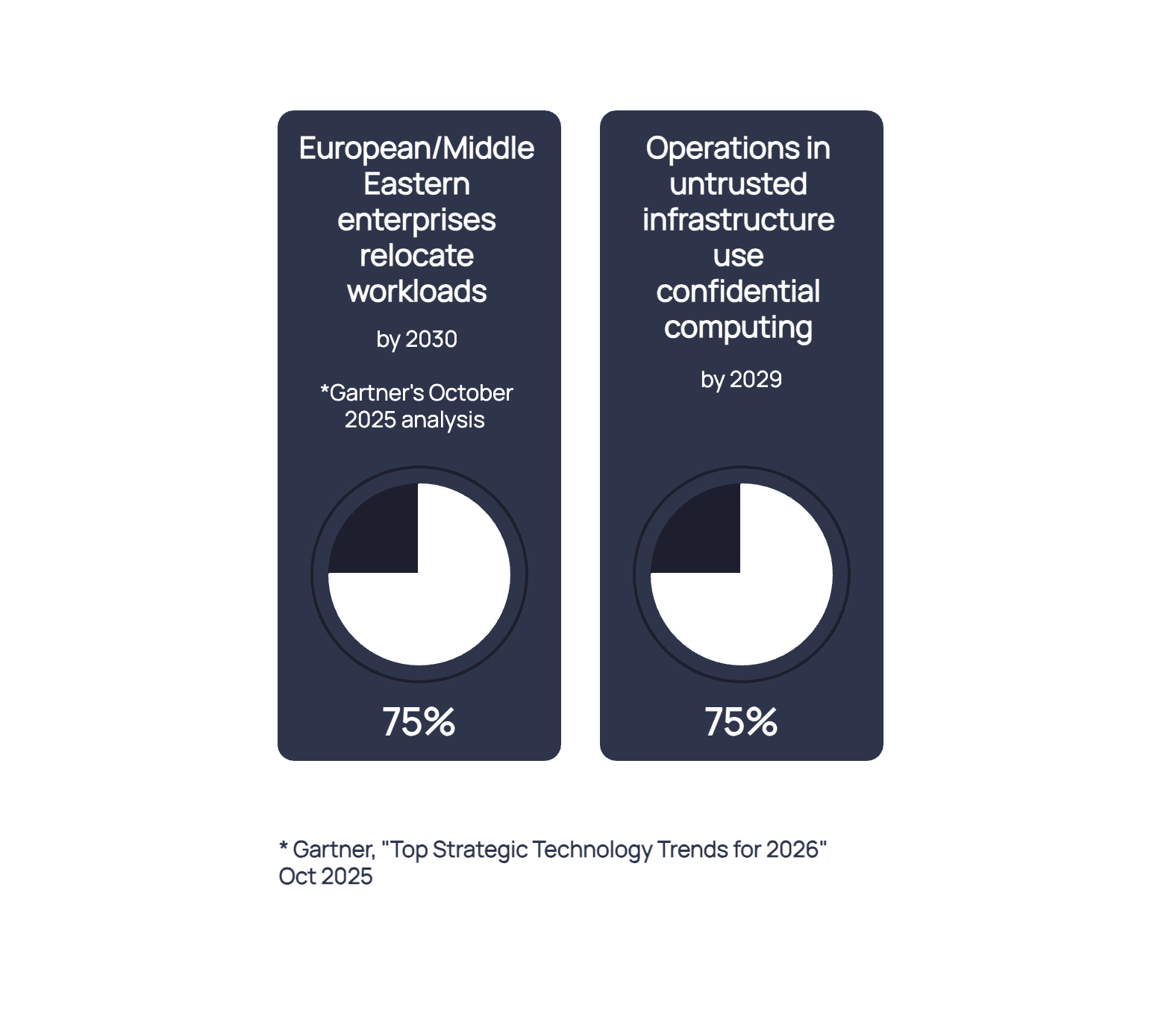
Gartner's October 2025 analysis shows 75% of European and Middle Eastern enterprises will relocate virtual workloads to reduce geopolitical risk by 2030, up from less than 5% in 2025.
The IBM Cost of a Data Breach Report 2025 reveals breaches involving multiple environments cost $5.05 million on average, versus $4.44 million globally. Non-compliance in multi-cloud environments increases legal costs by 15-25%, directly impacting operating margins and shareholder value.
By 2029, Gartner predicts 75% of operations in untrusted infrastructure will use confidential computing. Traditional perimeter-based cloud security no longer works in distributed environments.
What is cloud compliance and why is it critical in 2026?
Cloud compliance means your cloud services meet legal, regulatory, and industry requirements. When storing customer data or running applications in cloud infrastructure, you must prove cloud compliance with relevant standards.
The regulatory environment has expanded. GDPR governs EU data handling. HIPAA mandates health information safeguards. SOC 2 provides security frameworks for cloud services. NIS2 establishes cybersecurity requirements for European infrastructure. Organizations typically maintain cloud compliance across multiple frameworks simultaneously.
Cloud compliance extends beyond avoiding fines. Your cloud security strategy and compliance posture affect customer trust and competitive positioning. Prospects demand cloud security compliance evidence before contracts. Insurers adjust premiums based on certifications.
The 2026 environment introduces complexity for cloud compliance. Regulations targeting data residency and cross-border transfers take effect. Cloud providers expand certifications, but configuration responsibility remains yours.
Data security requires continuous attention. Threats evolve faster than regulations. Cloud compliance isn't a project but ongoing discipline as your cloud infrastructure grows. Your cloud security strategy must adapt constantly.
The cost of non-compliance in cloud environments
Cloud compliance failure costs extend beyond regulatory fines. Understanding full consequences justifies required investment.
Financial penalties vary widely. GDPR fines reach €20 million or 4% of revenue. HIPAA penalties reach $1.5 million annually. State attorneys general increasingly enforce privacy regulations aggressively.
Beyond fines, IBM breach data shows organizations pay $5.05 million on average when breaches span multiple environments. Costs include incident response, notification, legal fees, and investigations.
Customer trust erosion often proves more damaging. B2B customers may terminate contracts. Consumer-facing businesses see account deletions. Rebuilding trust takes years.
Competitive disadvantage emerges as prospects eliminate non-compliant vendors. Enterprise sales require security questionnaires and cloud compliance certifications. Organizations lacking cloud security compliance lose opportunities to competitors.
Legal exposure multiplies through class-action lawsuits. Shareholders sue over stock impacts. Customers sue over exposed information. Defense costs accumulate even when companies ultimately prevail.
Essential cloud compliance standards and regulations you need to know
Understanding applicable standards is foundational. Industry-specific regulations establish baseline requirements. HIPAA governs U.S. healthcare organizations. PCI DSS applies to payment processing. SOX affects publicly traded companies.
Privacy regulations have proliferated globally. GDPR remains most comprehensive, affecting any organization processing EU resident data. CCPA and CPRA give California residents similar rights. Brazil's LGPD, Canada's PIPEDA, and laws in dozens of countries create overlapping requirements.
Cloud security frameworks provide structured approaches. NIST offers a risk-based methodology. ISO/IEC 27001 specifies information security management requirements. The Cloud Security Alliance publishes the Cloud Controls Matrix.
Regional regulations emerge rapidly. NIS2 establishes requirements for EU critical infrastructure. DORA targets European financial services. Australia's Privacy Act creates obligations for Australian data handling.
Regulation/Standard | Jurisdiction | Key Requirements | Penalties |
GDPR | European Union | Data minimization, consent, breach notification | Up to €20M or 4% revenue |
HIPAA | U.S. Healthcare | Access controls, encryption, audit trails | Up to $1.5M annually |
SOC 2 | Global | Security, availability controls | Loss of certification |
PCI DSS | Global Payments | Network security, encryption | Up to $100K monthly |
Main cloud compliance challenges organizations face today
Organizations struggle with cloud compliance for interconnected reasons. Laws vary between countries, states, and municipalities. A company in California, New York, and Texas navigates three distinct privacy regimes before considering international regulations.
Data sovereignty requirements force difficult architectural decisions. Some regulations mandate data remain within geographic boundaries. When using a global cloud provider, understanding where data resides requires careful configuration.
The shared responsibility model creates ambiguity. Cloud providers secure infrastructure; customers secure what they build on it. Misunderstandings about these divisions cause significant compliance failures:
Encryption key management often falls into a gray area where both parties assume the other handles it properly
Access control verification requires customers to implement least privilege, but many don't understand their full responsibility
Logging configuration must capture sufficient audit detail, yet default settings rarely meet regulatory requirements without customization
Multi-cloud strategies amplify challenges. Each cloud provider offers different compliance tools and varying regulatory support. Organizations running workloads across three platforms must maintain expertise in three frameworks.
Resource constraints limit achievement. Cloud security expertise commands premium compensation. Even large organizations struggle with regulatory changes and new cloud services requiring evaluation.
How does the shared responsibility model work in cloud compliance?
The shared responsibility model defines accountability in cloud environments. This division remains poorly understood, leading to compliance failures.
Cloud providers handle infrastructure. They secure physical data centers, manage hardware, maintain networks, and patch virtualization platforms. For IaaS, providers ensure compute and storage function securely. PaaS adds operating system management. SaaS includes application-level security.
The model shifts by service type. In IaaS environments like AWS EC2, customers handle almost everything above the hypervisor: patching, firewalls, access management, encryption. PaaS reduces customer responsibilities, but you control data encryption and access policies. With SaaS, providers manage most security, yet customers configure properly and manage users.
What always remains customer responsibility: data classification and protection, identity and access management, compliance validation. Using a compliant cloud provider doesn't make you compliant automatically.
Common misconceptions cause problems. Some assume provider certifications equal automatic compliance. Incorrect. Others believe encryption is enabled automatically. Many cloud services require explicit encryption configuration.
Successful organizations document compliance requirements mapped to specific responsibilities. They train teams on the shared responsibility model and conduct regular audits verifying configurations remain compliant.
Implementing effective cloud governance in your organization
Cloud governance provides frameworks for decisions about cloud strategy, architecture, and cloud compliance. Without cloud governance, cloud usage becomes chaotic.
Start with clear policies defining permitted activities in cloud compliance. Which cloud services can teams use? What security controls must be enabled? Policies should guide decisions while accommodating business needs.
Implement policy enforcement through technical controls. AWS Organizations, Azure Policy, and Google Cloud Organization Policy prevent configurations violating cloud compliance standards. When developers try creating unencrypted databases, these controls block automatically.
Establish approval workflows for sensitive operations. Creating cloud accounts or accessing production data should trigger appropriate review for cloud governance.
Least privilege forms the access control foundation. Users need only required permissions. Review and adjust as roles change.
Centralized logging enables cloud governance oversight. Every cloud infrastructure action should generate logs capturing who did what when.
Tag resources consistently. Tags identifying owner, project, and cloud compliance requirements enable automated enforcement.
What best practices ensure cloud compliance and data security?
Maintaining cloud compliance requires proven practices across people, processes, and technology.
Understand cloud compliance requirements comprehensively before architectural decisions. Map applicable standards, then design your cloud strategy to address them systematically. Retrofitting cloud compliance costs far more.
Implement encryption for data in transit and at rest. Modern cloud providers make encryption straightforward, but it requires explicit configuration. Use strong algorithms and proper key management.
Enforce multi-factor authentication across all cloud accounts. Compromised credentials remain the leading cause of cloud security incidents. Multi-factor authentication blocks most credential-based attacks.
Adopt least privilege rigorously. Users should have only required access. Review permissions quarterly and revoke unneeded access. Implement time-bound access for privileged operations.
Enable comprehensive logging and centralize storage. Every action should generate log entries. Store logs separately to prevent tampering.
Automate cloud compliance monitoring for continuous visibility. Manual cloud audits cannot keep pace with cloud infrastructure change rates. Automated tools scan continuously and alert when drift occurs.
For organizations pursuing secure cloud migration, establish cloud governance frameworks before migration begins. Define your target state for cloud compliance upfront.
When operating multi-cloud environments, consider these essential practices that distinguish mature cloud security programs from basic implementations:
Standardize security controls across cloud providers wherever technically feasible to reduce expertise burden
Use infrastructure-as-code for consistent configurations, ensuring cloud compliance settings don't drift between environments
Centralize identity management through a single directory service that federates to all platforms
Implement cross-cloud monitoring dashboards that provide unified visibility into cloud security posture
Segment cloud networks logically to contain breaches and comply with data residency requirements. Create separate virtual networks for different security zones.
Conduct regular tabletop exercises simulating cloud compliance incidents. Practice responding to regulatory inquiries and breach notifications.
Maintain comprehensive documentation of cloud architecture, security controls, and cloud compliance processes. Documentation must be detailed enough for cloud audits to proceed smoothly.
Organizations building compliance-ready cloud infrastructure from the beginning avoid costly remediation later.
Steps to audit your cloud environment for compliance
Effective cloud audit processes combine automated tools with expert analysis. Define your cloud audit scope clearly: which cloud services, what compliance frameworks, what time period. Focused cloud audits thoroughly examine specific aspects of cloud compliance.
Inventory cloud resources comprehensively. Shadow IT and forgotten test environments create compliance blind spots. Use cloud-native inventory tools across all accounts and regions.
Map resources to compliance controls systematically. For each regulation, identify required controls. Trace how your cloud infrastructure implements them.
Automated scanning provides continuous visibility. AWS Security Hub, Azure Security Center, and Google Cloud Security Command Center assess configurations against benchmarks. Third-party tools offer additional capabilities. However, automation has limits. Tools verify encryption is enabled but not whether you're encrypting the right data.
Manual review remains essential. Examine data flows for residency compliance. Review access permissions for least privilege. Analyze incident response procedures for notification timelines.
Third-party audits provide independent validation. Consider engaging a compliance audit firm with cloud expertise.
Audit Phase | Key Activities | Frequency |
Scoping | Define boundaries, identify regulations | Annually |
Discovery | Inventory resources, map data flows | Continuously |
Assessment | Test controls, review configurations | Quarterly automated, annual comprehensive |
Remediation | Fix issues, update policies | Ongoing |
How is cloud compliance evolving: what to expect in 2026 and beyond?
Cloud compliance will evolve significantly as technology, regulations, and geopolitics converge. Organizations must prepare for fundamental shifts across multiple dimensions.
Technology advances are reshaping security architectures:
Automation in cloud compliance monitoring will advance rapidly, with policy-as-code frameworks defining requirements declaratively and enforcing them continuously
Confidential computing moves from niche to mainstream, protecting data during processing rather than just at rest
Zero trust architecture will evolve from aspiration to standard practice for cloud security, replacing traditional perimeter-based approaches that fail where boundaries are fluid
Geopolitical and regulatory pressures intensify:
Data sovereignty concerns drive enterprises to relocate workloads closer to home, reversing years of global cloud consolidation
Cross-border data transfer regulations will become more complex, forcing organizations to design cloud strategy accommodating varying localization requirements
Compliance transforms from cost center to competitive differentiator, with organizations lacking strong cloud security compliance losing market opportunities
The gap between cloud adoption speed and governance maturity creates risk. Organizations rushing to implement new cloud services without proper compliance frameworks expose themselves to regulatory violations and security incidents. Success requires embedding cloud compliance into architecture decisions from the start, not retrofitting controls afterward.
Contact Streamlogic for a compliance assessment to ensure your cloud infrastructure is prepared for regulatory changes ahead.

Denis Avramenko
CTO, Co-Founder, Streamlogic


Technology Articles
Cloud Modernization Strategy Guide for Enterprises 2026
Dec 18, 2025


Technology Articles
How to Develop Cloud Applications: Complete Planning to Deployment Roadmap 2026
Dec 18, 2025


Technology Articles
Cloud Compliance in 2026: Navigating Standards, Strategies, and Best Practices
Dec 12, 2025


Technology Articles
Cloud Modernization Strategy Guide for Enterprises 2026
Dec 18, 2025


Technology Articles
How to Develop Cloud Applications: Complete Planning to Deployment Roadmap 2026
Dec 18, 2025


Technology Articles
Cloud Compliance in 2026: Navigating Standards, Strategies, and Best Practices
Dec 12, 2025
Table of Contents
Key insights: cloud compliance in 2026
What is cloud compliance and why is it critical in 2026?
The cost of non-compliance in cloud environments
Essential cloud compliance standards and regulations you need to know
Main cloud compliance challenges organizations face today
How does the shared responsibility model work in cloud compliance?
Implementing effective cloud governance in your organization
What best practices ensure cloud compliance and data security?
Steps to audit your cloud environment for compliance
How is cloud compliance evolving: what to expect in 2026 and beyond?
Key insights: cloud compliance in 2026
Companies face mounting pressure to demonstrate their cloud infrastructure meets security and privacy requirements, as customers increasingly require proof of regulatory adherence before finalizing agreements.
Gartner's October 2025 analysis shows 75% of European and Middle Eastern enterprises will relocate virtual workloads to reduce geopolitical risk by 2030, up from less than 5% in 2025.
The IBM Cost of a Data Breach Report 2025 reveals breaches involving multiple environments cost $5.05 million on average, versus $4.44 million globally. Non-compliance in multi-cloud environments increases legal costs by 15-25%, directly impacting operating margins and shareholder value.
By 2029, Gartner predicts 75% of operations in untrusted infrastructure will use confidential computing. Traditional perimeter-based cloud security no longer works in distributed environments.

What is cloud compliance and why is it critical in 2026?
Cloud compliance means your cloud services meet legal, regulatory, and industry requirements. When storing customer data or running applications in cloud infrastructure, you must prove cloud compliance with relevant standards.
The regulatory environment has expanded. GDPR governs EU data handling. HIPAA mandates health information safeguards. SOC 2 provides security frameworks for cloud services. NIS2 establishes cybersecurity requirements for European infrastructure. Organizations typically maintain cloud compliance across multiple frameworks simultaneously.
Cloud compliance extends beyond avoiding fines. Your cloud security strategy and compliance posture affect customer trust and competitive positioning. Prospects demand cloud security compliance evidence before contracts. Insurers adjust premiums based on certifications.
The 2026 environment introduces complexity for cloud compliance. Regulations targeting data residency and cross-border transfers take effect. Cloud providers expand certifications, but configuration responsibility remains yours.
Data security requires continuous attention. Threats evolve faster than regulations. Cloud compliance isn't a project but ongoing discipline as your cloud infrastructure grows. Your cloud security strategy must adapt constantly.
The cost of non-compliance in cloud environments
Cloud compliance failure costs extend beyond regulatory fines. Understanding full consequences justifies required investment.
Financial penalties vary widely. GDPR fines reach €20 million or 4% of revenue. HIPAA penalties reach $1.5 million annually. State attorneys general increasingly enforce privacy regulations aggressively.
Beyond fines, IBM breach data shows organizations pay $5.05 million on average when breaches span multiple environments. Costs include incident response, notification, legal fees, and investigations.
Customer trust erosion often proves more damaging. B2B customers may terminate contracts. Consumer-facing businesses see account deletions. Rebuilding trust takes years.
Competitive disadvantage emerges as prospects eliminate non-compliant vendors. Enterprise sales require security questionnaires and cloud compliance certifications. Organizations lacking cloud security compliance lose opportunities to competitors.
Legal exposure multiplies through class-action lawsuits. Shareholders sue over stock impacts. Customers sue over exposed information. Defense costs accumulate even when companies ultimately prevail.
Essential cloud compliance standards and regulations you need to know
Understanding applicable standards is foundational. Industry-specific regulations establish baseline requirements. HIPAA governs U.S. healthcare organizations. PCI DSS applies to payment processing. SOX affects publicly traded companies.
Privacy regulations have proliferated globally. GDPR remains most comprehensive, affecting any organization processing EU resident data. CCPA and CPRA give California residents similar rights. Brazil's LGPD, Canada's PIPEDA, and laws in dozens of countries create overlapping requirements.
Cloud security frameworks provide structured approaches. NIST offers a risk-based methodology. ISO/IEC 27001 specifies information security management requirements. The Cloud Security Alliance publishes the Cloud Controls Matrix.
Regional regulations emerge rapidly. NIS2 establishes requirements for EU critical infrastructure. DORA targets European financial services. Australia's Privacy Act creates obligations for Australian data handling.
Regulation/Standard | Jurisdiction | Key Requirements | Penalties |
GDPR | European Union | Data minimization, consent, breach notification | Up to €20M or 4% revenue |
HIPAA | U.S. Healthcare | Access controls, encryption, audit trails | Up to $1.5M annually |
SOC 2 | Global | Security, availability controls | Loss of certification |
PCI DSS | Global Payments | Network security, encryption | Up to $100K monthly |
Main cloud compliance challenges organizations face today
Organizations struggle with cloud compliance for interconnected reasons. Laws vary between countries, states, and municipalities. A company in California, New York, and Texas navigates three distinct privacy regimes before considering international regulations.
Data sovereignty requirements force difficult architectural decisions. Some regulations mandate data remain within geographic boundaries. When using a global cloud provider, understanding where data resides requires careful configuration.
The shared responsibility model creates ambiguity. Cloud providers secure infrastructure; customers secure what they build on it. Misunderstandings about these divisions cause significant compliance failures:
Encryption key management often falls into a gray area where both parties assume the other handles it properly
Access control verification requires customers to implement least privilege, but many don't understand their full responsibility
Logging configuration must capture sufficient audit detail, yet default settings rarely meet regulatory requirements without customization
Multi-cloud strategies amplify challenges. Each cloud provider offers different compliance tools and varying regulatory support. Organizations running workloads across three platforms must maintain expertise in three frameworks.
Resource constraints limit achievement. Cloud security expertise commands premium compensation. Even large organizations struggle with regulatory changes and new cloud services requiring evaluation.
How does the shared responsibility model work in cloud compliance?
The shared responsibility model defines accountability in cloud environments. This division remains poorly understood, leading to compliance failures.
Cloud providers handle infrastructure. They secure physical data centers, manage hardware, maintain networks, and patch virtualization platforms. For IaaS, providers ensure compute and storage function securely. PaaS adds operating system management. SaaS includes application-level security.
The model shifts by service type. In IaaS environments like AWS EC2, customers handle almost everything above the hypervisor: patching, firewalls, access management, encryption. PaaS reduces customer responsibilities, but you control data encryption and access policies. With SaaS, providers manage most security, yet customers configure properly and manage users.
What always remains customer responsibility: data classification and protection, identity and access management, compliance validation. Using a compliant cloud provider doesn't make you compliant automatically.
Common misconceptions cause problems. Some assume provider certifications equal automatic compliance. Incorrect. Others believe encryption is enabled automatically. Many cloud services require explicit encryption configuration.
Successful organizations document compliance requirements mapped to specific responsibilities. They train teams on the shared responsibility model and conduct regular audits verifying configurations remain compliant.
Implementing effective cloud governance in your organization
Cloud governance provides frameworks for decisions about cloud strategy, architecture, and cloud compliance. Without cloud governance, cloud usage becomes chaotic.
Start with clear policies defining permitted activities in cloud compliance. Which cloud services can teams use? What security controls must be enabled? Policies should guide decisions while accommodating business needs.
Implement policy enforcement through technical controls. AWS Organizations, Azure Policy, and Google Cloud Organization Policy prevent configurations violating cloud compliance standards. When developers try creating unencrypted databases, these controls block automatically.
Establish approval workflows for sensitive operations. Creating cloud accounts or accessing production data should trigger appropriate review for cloud governance.
Least privilege forms the access control foundation. Users need only required permissions. Review and adjust as roles change.
Centralized logging enables cloud governance oversight. Every cloud infrastructure action should generate logs capturing who did what when.
Tag resources consistently. Tags identifying owner, project, and cloud compliance requirements enable automated enforcement.
What best practices ensure cloud compliance and data security?

Maintaining cloud compliance requires proven practices across people, processes, and technology.
Understand cloud compliance requirements comprehensively before architectural decisions. Map applicable standards, then design your cloud strategy to address them systematically. Retrofitting cloud compliance costs far more.
Implement encryption for data in transit and at rest. Modern cloud providers make encryption straightforward, but it requires explicit configuration. Use strong algorithms and proper key management.
Enforce multi-factor authentication across all cloud accounts. Compromised credentials remain the leading cause of cloud security incidents. Multi-factor authentication blocks most credential-based attacks.
Adopt least privilege rigorously. Users should have only required access. Review permissions quarterly and revoke unneeded access. Implement time-bound access for privileged operations.
Enable comprehensive logging and centralize storage. Every action should generate log entries. Store logs separately to prevent tampering.
Automate cloud compliance monitoring for continuous visibility. Manual cloud audits cannot keep pace with cloud infrastructure change rates. Automated tools scan continuously and alert when drift occurs.
For organizations pursuing secure cloud migration, establish cloud governance frameworks before migration begins. Define your target state for cloud compliance upfront.
When operating multi-cloud environments, consider these essential practices that distinguish mature cloud security programs from basic implementations:
Standardize security controls across cloud providers wherever technically feasible to reduce expertise burden
Use infrastructure-as-code for consistent configurations, ensuring cloud compliance settings don't drift between environments
Centralize identity management through a single directory service that federates to all platforms
Implement cross-cloud monitoring dashboards that provide unified visibility into cloud security posture
Segment cloud networks logically to contain breaches and comply with data residency requirements. Create separate virtual networks for different security zones.
Conduct regular tabletop exercises simulating cloud compliance incidents. Practice responding to regulatory inquiries and breach notifications.
Maintain comprehensive documentation of cloud architecture, security controls, and cloud compliance processes. Documentation must be detailed enough for cloud audits to proceed smoothly.
Organizations building compliance-ready cloud infrastructure from the beginning avoid costly remediation later.
Steps to audit your cloud environment for compliance
Effective cloud audit processes combine automated tools with expert analysis. Define your cloud audit scope clearly: which cloud services, what compliance frameworks, what time period. Focused cloud audits thoroughly examine specific aspects of cloud compliance.
Inventory cloud resources comprehensively. Shadow IT and forgotten test environments create compliance blind spots. Use cloud-native inventory tools across all accounts and regions.
Map resources to compliance controls systematically. For each regulation, identify required controls. Trace how your cloud infrastructure implements them.
Automated scanning provides continuous visibility. AWS Security Hub, Azure Security Center, and Google Cloud Security Command Center assess configurations against benchmarks. Third-party tools offer additional capabilities. However, automation has limits. Tools verify encryption is enabled but not whether you're encrypting the right data.
Manual review remains essential. Examine data flows for residency compliance. Review access permissions for least privilege. Analyze incident response procedures for notification timelines.
Third-party audits provide independent validation. Consider engaging a compliance audit firm with cloud expertise.
Audit Phase | Key Activities | Frequency |
Scoping | Define boundaries, identify regulations | Annually |
Discovery | Inventory resources, map data flows | Continuously |
Assessment | Test controls, review configurations | Quarterly automated, annual comprehensive |
Remediation | Fix issues, update policies | Ongoing |
How is cloud compliance evolving: what to expect in 2026 and beyond?
Cloud compliance will evolve significantly as technology, regulations, and geopolitics converge. Organizations must prepare for fundamental shifts across multiple dimensions.
Technology advances are reshaping security architectures:
Automation in cloud compliance monitoring will advance rapidly, with policy-as-code frameworks defining requirements declaratively and enforcing them continuously
Confidential computing moves from niche to mainstream, protecting data during processing rather than just at rest
Zero trust architecture will evolve from aspiration to standard practice for cloud security, replacing traditional perimeter-based approaches that fail where boundaries are fluid
Geopolitical and regulatory pressures intensify:
Data sovereignty concerns drive enterprises to relocate workloads closer to home, reversing years of global cloud consolidation
Cross-border data transfer regulations will become more complex, forcing organizations to design cloud strategy accommodating varying localization requirements
Compliance transforms from cost center to competitive differentiator, with organizations lacking strong cloud security compliance losing market opportunities
The gap between cloud adoption speed and governance maturity creates risk. Organizations rushing to implement new cloud services without proper compliance frameworks expose themselves to regulatory violations and security incidents. Success requires embedding cloud compliance into architecture decisions from the start, not retrofitting controls afterward.
Contact Streamlogic for a compliance assessment to ensure your cloud infrastructure is prepared for regulatory changes ahead.

Denis Avramenko
CTO, Co-Founder, Streamlogic
Table of Contents
Key insights: cloud compliance in 2026
What is cloud compliance and why is it critical in 2026?
The cost of non-compliance in cloud environments
Essential cloud compliance standards and regulations you need to know
Main cloud compliance challenges organizations face today
How does the shared responsibility model work in cloud compliance?
Implementing effective cloud governance in your organization
What best practices ensure cloud compliance and data security?
Steps to audit your cloud environment for compliance
How is cloud compliance evolving: what to expect in 2026 and beyond?
Key insights: cloud compliance in 2026
Companies face mounting pressure to demonstrate their cloud infrastructure meets security and privacy requirements, as customers increasingly require proof of regulatory adherence before finalizing agreements.
Gartner's October 2025 analysis shows 75% of European and Middle Eastern enterprises will relocate virtual workloads to reduce geopolitical risk by 2030, up from less than 5% in 2025.
The IBM Cost of a Data Breach Report 2025 reveals breaches involving multiple environments cost $5.05 million on average, versus $4.44 million globally. Non-compliance in multi-cloud environments increases legal costs by 15-25%, directly impacting operating margins and shareholder value.
By 2029, Gartner predicts 75% of operations in untrusted infrastructure will use confidential computing. Traditional perimeter-based cloud security no longer works in distributed environments.

What is cloud compliance and why is it critical in 2026?
Cloud compliance means your cloud services meet legal, regulatory, and industry requirements. When storing customer data or running applications in cloud infrastructure, you must prove cloud compliance with relevant standards.
The regulatory environment has expanded. GDPR governs EU data handling. HIPAA mandates health information safeguards. SOC 2 provides security frameworks for cloud services. NIS2 establishes cybersecurity requirements for European infrastructure. Organizations typically maintain cloud compliance across multiple frameworks simultaneously.
Cloud compliance extends beyond avoiding fines. Your cloud security strategy and compliance posture affect customer trust and competitive positioning. Prospects demand cloud security compliance evidence before contracts. Insurers adjust premiums based on certifications.
The 2026 environment introduces complexity for cloud compliance. Regulations targeting data residency and cross-border transfers take effect. Cloud providers expand certifications, but configuration responsibility remains yours.
Data security requires continuous attention. Threats evolve faster than regulations. Cloud compliance isn't a project but ongoing discipline as your cloud infrastructure grows. Your cloud security strategy must adapt constantly.
The cost of non-compliance in cloud environments
Cloud compliance failure costs extend beyond regulatory fines. Understanding full consequences justifies required investment.
Financial penalties vary widely. GDPR fines reach €20 million or 4% of revenue. HIPAA penalties reach $1.5 million annually. State attorneys general increasingly enforce privacy regulations aggressively.
Beyond fines, IBM breach data shows organizations pay $5.05 million on average when breaches span multiple environments. Costs include incident response, notification, legal fees, and investigations.
Customer trust erosion often proves more damaging. B2B customers may terminate contracts. Consumer-facing businesses see account deletions. Rebuilding trust takes years.
Competitive disadvantage emerges as prospects eliminate non-compliant vendors. Enterprise sales require security questionnaires and cloud compliance certifications. Organizations lacking cloud security compliance lose opportunities to competitors.
Legal exposure multiplies through class-action lawsuits. Shareholders sue over stock impacts. Customers sue over exposed information. Defense costs accumulate even when companies ultimately prevail.
Essential cloud compliance standards and regulations you need to know
Understanding applicable standards is foundational. Industry-specific regulations establish baseline requirements. HIPAA governs U.S. healthcare organizations. PCI DSS applies to payment processing. SOX affects publicly traded companies.
Privacy regulations have proliferated globally. GDPR remains most comprehensive, affecting any organization processing EU resident data. CCPA and CPRA give California residents similar rights. Brazil's LGPD, Canada's PIPEDA, and laws in dozens of countries create overlapping requirements.
Cloud security frameworks provide structured approaches. NIST offers a risk-based methodology. ISO/IEC 27001 specifies information security management requirements. The Cloud Security Alliance publishes the Cloud Controls Matrix.
Regional regulations emerge rapidly. NIS2 establishes requirements for EU critical infrastructure. DORA targets European financial services. Australia's Privacy Act creates obligations for Australian data handling.
Regulation/Standard | Jurisdiction | Key Requirements | Penalties |
GDPR | European Union | Data minimization, consent, breach notification | Up to €20M or 4% revenue |
HIPAA | U.S. Healthcare | Access controls, encryption, audit trails | Up to $1.5M annually |
SOC 2 | Global | Security, availability controls | Loss of certification |
PCI DSS | Global Payments | Network security, encryption | Up to $100K monthly |
Main cloud compliance challenges organizations face today
Organizations struggle with cloud compliance for interconnected reasons. Laws vary between countries, states, and municipalities. A company in California, New York, and Texas navigates three distinct privacy regimes before considering international regulations.
Data sovereignty requirements force difficult architectural decisions. Some regulations mandate data remain within geographic boundaries. When using a global cloud provider, understanding where data resides requires careful configuration.
The shared responsibility model creates ambiguity. Cloud providers secure infrastructure; customers secure what they build on it. Misunderstandings about these divisions cause significant compliance failures:
Encryption key management often falls into a gray area where both parties assume the other handles it properly
Access control verification requires customers to implement least privilege, but many don't understand their full responsibility
Logging configuration must capture sufficient audit detail, yet default settings rarely meet regulatory requirements without customization
Multi-cloud strategies amplify challenges. Each cloud provider offers different compliance tools and varying regulatory support. Organizations running workloads across three platforms must maintain expertise in three frameworks.
Resource constraints limit achievement. Cloud security expertise commands premium compensation. Even large organizations struggle with regulatory changes and new cloud services requiring evaluation.
How does the shared responsibility model work in cloud compliance?
The shared responsibility model defines accountability in cloud environments. This division remains poorly understood, leading to compliance failures.
Cloud providers handle infrastructure. They secure physical data centers, manage hardware, maintain networks, and patch virtualization platforms. For IaaS, providers ensure compute and storage function securely. PaaS adds operating system management. SaaS includes application-level security.
The model shifts by service type. In IaaS environments like AWS EC2, customers handle almost everything above the hypervisor: patching, firewalls, access management, encryption. PaaS reduces customer responsibilities, but you control data encryption and access policies. With SaaS, providers manage most security, yet customers configure properly and manage users.
What always remains customer responsibility: data classification and protection, identity and access management, compliance validation. Using a compliant cloud provider doesn't make you compliant automatically.
Common misconceptions cause problems. Some assume provider certifications equal automatic compliance. Incorrect. Others believe encryption is enabled automatically. Many cloud services require explicit encryption configuration.
Successful organizations document compliance requirements mapped to specific responsibilities. They train teams on the shared responsibility model and conduct regular audits verifying configurations remain compliant.
Implementing effective cloud governance in your organization
Cloud governance provides frameworks for decisions about cloud strategy, architecture, and cloud compliance. Without cloud governance, cloud usage becomes chaotic.
Start with clear policies defining permitted activities in cloud compliance. Which cloud services can teams use? What security controls must be enabled? Policies should guide decisions while accommodating business needs.
Implement policy enforcement through technical controls. AWS Organizations, Azure Policy, and Google Cloud Organization Policy prevent configurations violating cloud compliance standards. When developers try creating unencrypted databases, these controls block automatically.
Establish approval workflows for sensitive operations. Creating cloud accounts or accessing production data should trigger appropriate review for cloud governance.
Least privilege forms the access control foundation. Users need only required permissions. Review and adjust as roles change.
Centralized logging enables cloud governance oversight. Every cloud infrastructure action should generate logs capturing who did what when.
Tag resources consistently. Tags identifying owner, project, and cloud compliance requirements enable automated enforcement.
What best practices ensure cloud compliance and data security?

Maintaining cloud compliance requires proven practices across people, processes, and technology.
Understand cloud compliance requirements comprehensively before architectural decisions. Map applicable standards, then design your cloud strategy to address them systematically. Retrofitting cloud compliance costs far more.
Implement encryption for data in transit and at rest. Modern cloud providers make encryption straightforward, but it requires explicit configuration. Use strong algorithms and proper key management.
Enforce multi-factor authentication across all cloud accounts. Compromised credentials remain the leading cause of cloud security incidents. Multi-factor authentication blocks most credential-based attacks.
Adopt least privilege rigorously. Users should have only required access. Review permissions quarterly and revoke unneeded access. Implement time-bound access for privileged operations.
Enable comprehensive logging and centralize storage. Every action should generate log entries. Store logs separately to prevent tampering.
Automate cloud compliance monitoring for continuous visibility. Manual cloud audits cannot keep pace with cloud infrastructure change rates. Automated tools scan continuously and alert when drift occurs.
For organizations pursuing secure cloud migration, establish cloud governance frameworks before migration begins. Define your target state for cloud compliance upfront.
When operating multi-cloud environments, consider these essential practices that distinguish mature cloud security programs from basic implementations:
Standardize security controls across cloud providers wherever technically feasible to reduce expertise burden
Use infrastructure-as-code for consistent configurations, ensuring cloud compliance settings don't drift between environments
Centralize identity management through a single directory service that federates to all platforms
Implement cross-cloud monitoring dashboards that provide unified visibility into cloud security posture
Segment cloud networks logically to contain breaches and comply with data residency requirements. Create separate virtual networks for different security zones.
Conduct regular tabletop exercises simulating cloud compliance incidents. Practice responding to regulatory inquiries and breach notifications.
Maintain comprehensive documentation of cloud architecture, security controls, and cloud compliance processes. Documentation must be detailed enough for cloud audits to proceed smoothly.
Organizations building compliance-ready cloud infrastructure from the beginning avoid costly remediation later.
Steps to audit your cloud environment for compliance
Effective cloud audit processes combine automated tools with expert analysis. Define your cloud audit scope clearly: which cloud services, what compliance frameworks, what time period. Focused cloud audits thoroughly examine specific aspects of cloud compliance.
Inventory cloud resources comprehensively. Shadow IT and forgotten test environments create compliance blind spots. Use cloud-native inventory tools across all accounts and regions.
Map resources to compliance controls systematically. For each regulation, identify required controls. Trace how your cloud infrastructure implements them.
Automated scanning provides continuous visibility. AWS Security Hub, Azure Security Center, and Google Cloud Security Command Center assess configurations against benchmarks. Third-party tools offer additional capabilities. However, automation has limits. Tools verify encryption is enabled but not whether you're encrypting the right data.
Manual review remains essential. Examine data flows for residency compliance. Review access permissions for least privilege. Analyze incident response procedures for notification timelines.
Third-party audits provide independent validation. Consider engaging a compliance audit firm with cloud expertise.
Audit Phase | Key Activities | Frequency |
Scoping | Define boundaries, identify regulations | Annually |
Discovery | Inventory resources, map data flows | Continuously |
Assessment | Test controls, review configurations | Quarterly automated, annual comprehensive |
Remediation | Fix issues, update policies | Ongoing |
How is cloud compliance evolving: what to expect in 2026 and beyond?
Cloud compliance will evolve significantly as technology, regulations, and geopolitics converge. Organizations must prepare for fundamental shifts across multiple dimensions.
Technology advances are reshaping security architectures:
Automation in cloud compliance monitoring will advance rapidly, with policy-as-code frameworks defining requirements declaratively and enforcing them continuously
Confidential computing moves from niche to mainstream, protecting data during processing rather than just at rest
Zero trust architecture will evolve from aspiration to standard practice for cloud security, replacing traditional perimeter-based approaches that fail where boundaries are fluid
Geopolitical and regulatory pressures intensify:
Data sovereignty concerns drive enterprises to relocate workloads closer to home, reversing years of global cloud consolidation
Cross-border data transfer regulations will become more complex, forcing organizations to design cloud strategy accommodating varying localization requirements
Compliance transforms from cost center to competitive differentiator, with organizations lacking strong cloud security compliance losing market opportunities
The gap between cloud adoption speed and governance maturity creates risk. Organizations rushing to implement new cloud services without proper compliance frameworks expose themselves to regulatory violations and security incidents. Success requires embedding cloud compliance into architecture decisions from the start, not retrofitting controls afterward.
Contact Streamlogic for a compliance assessment to ensure your cloud infrastructure is prepared for regulatory changes ahead.

Denis Avramenko
CTO, Co-Founder, Streamlogic


Technology Articles
Cloud Modernization Strategy Guide for Enterprises 2026
Dec 18, 2025


Technology Articles
How to Develop Cloud Applications: Complete Planning to Deployment Roadmap 2026
Dec 18, 2025


Technology Articles
Cloud Compliance in 2026: Navigating Standards, Strategies, and Best Practices
Dec 12, 2025
Tech Council
Technology Articles
Cloud Compliance in 2026: Navigating Standards, Strategies, and Best Practices
Learn regulatory frameworks, shared responsibility model, audit methodology, and multi-cloud security challenges. Breach cost data and 2026 trend analysis.

Denis Avramenko
CTO, Co-Founder, Streamlogic
Dec 12, 2025

